Author: Chizuru Toyama, TXOne Threat Research
Overview
This report presents telemetry data collected by our IoT/ICS Threat Intelligence platform concerning exploitation attempts targeting two critical vulnerabilities in SAP’s MetadataUploader service: CVE-2025-31324 and CVE-2025-42999.
- CVE-2025-31324 is an unauthenticated file upload vulnerability affecting the /developmentserver/metadatauploader endpoint. It enables remote attackers to upload malicious files—such as web shells—without authentication.
- CVE-2025-42999 is an insecure deserialization vulnerability that can be exploited by privileged attackers to execute arbitrary code.
In observed attack patterns, adversaries uploaded malicious files (e.g., JSP web shells and .properties files), which were accepted by the service and, in some cases, structured to trigger deserialization. This combined use of file upload and deserialization is intended to achieve remote code execution (RCE).
Notably, our telemetry captured .properties-based payloads as early as June 2025, decoded using ISO-8859-1, revealing serialized Java objects crafted for out-of-band (OOB) interaction testing. These were observed prior to the public release of a full exploit script on August 15 by a group identified as ShinyHunters, amplified by VX Underground (*1)(*2). These findings underscore the value of field telemetry in identifying attacker behavior ahead of public disclosures.
Vulnerability Status
- Severity: CVSS 3.1 score of 10.0 (Critical) for CVE-2025-31324 and 9.1 (Critical) and CVE-2025-42999.
- Active Exploitation: Initial reconnaissance and exploit testing were observed against honeypot networks in January 2025, followed by successful compromises reported by security firms, with attackers deploying web shells in March 2025.
- Affected Versions:
- CVE-2025-31324: All NetWeaver 7.xx versions, including Visual Composer with the VCFRAMEWORK component (version 7.50 and earlier)
- CVE-2025-42999: SAP NetWeaver version 7.5, particularly where Visual Composer is enabled; this typically includes default installations starting with NetWeaver 2004s
- KEV Listing: Added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on April 29, 2025, and May 15, 2025, for CVE-2025-31324 and CVE-2025-42999 respectively. These additions emphasize the urgent need for patching.
Notable Payloads Observed
Our IoT/ICS Threat Intelligence platform recorded multiple exploitation attempts targeting CVE-2025-31324. Below are details of the most notable payloads observed:
.jsp payload
- Source Country: Turkey, Germany
- Date: June 17, 2025; June 27, 2025
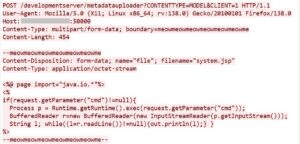
- Description: Attackers leveraged the vulnerable endpoint to upload a JSP web shell, enabling remote command execution via ?cmd=<command>.
- Impact: Successful execution of the web shell can grant attackers full control over the host. Subsequent activities may include system reconnaissance, lateral movement, and establishment of persistence.
.properties Payload
-
- Source Country: United States, Russia
- Date: June 2, 2025; July 4, 2025
- Description: Adversaries sent multipart/form-data POST requests to the endpoint /developmentserver/metadatauploader?CONTENTTYPE=MODEL&CLIENT=1, containing ZIP archives (identified by the PK\x03\x04 signature) disguised as .properties files. These payloads were crafted to test the server’s handling of serialized Java objects.
- Decoded Content: When decoded using ISO-8859-1, the payload revealed a serialized util.Propertiesobject containing a nested java.net.URL field pointing to an attacker-controlled domain (*.oast.online). This structure is commonly used for out-of-band (OOB) interaction testing, where the attacker watches out for callbacks to confirm whether the payload was processed.
Impact: Although the payload was not deserialized by the SAP MetadataUploader service in this instance, its structure strongly suggests an attempt to exploit both file uploading and insecure deserialization. If processed, it could result in remote code execution (RCE) via automatic resolution of the embedded URL.
Interestingly, although the public exploit was released on August 15, 2025, our IoT/ICS Threat Intelligence honeypots had already recorded similar payloads two months earlier. This indicates that adversaries were actively testing these techniques in the wild prior to public proof-of-concept (PoC) disclosure—likely targeting unpatched or poorly monitored systems.
This progression—from simple JSP web shells to more sophisticated serialized .properties payloads—demonstrates how attacker tradecraft evolves rapidly once an exploit becomes known. It underscores the importance of honeypot intelligence in detecting early-stage experimentation, giving defenders critical lead time to prepare before widespread exploitation begins.
Detection & Mitigation
-
- Apply Security Updates Immediately
-
-
- Refer to SAP Security Note #3594142 (*3)
- Refer to SAP Security Note #3604119 (*4)
-
-
- Restrict Access to Vulnerable Endpoints
-
-
- Use firewall rules or intrusion prevention systems (IPS) to block unauthorized access to /developmentserver/metadatauploader.
-
-
- Remove Vulnerable Components if Patching is Unfeasible
-
-
- Fully remove the sap.com/devserver_metadataupload_ear application from affected systems.
-
Conclusion
Our telemetry reveals that attackers began experimenting with serialized .properties payloads targeting CVE-2025-31324 as early as June 2025, well before the public release of a working exploit on August 15. These early payloads, decoded using ISO-8859-1, were crafted to trigger out-of-band (OOB) callbacks—indicating that adversaries were actively testing deserialization-based techniques in the wild.
This timeline suggests that proof-of-concept code was already circulating in underground communities, and that attackers were refining their methods before public disclosure. The shift from basic JSP web shells to more complex serialized payloads illustrate how quickly attacker tradecraft evolves once a vulnerability becomes known.
These findings underscore the importance of early telemetry and honeypot intelligence in identifying emerging threats, enabling defenders to respond proactively before widespread exploitation occurs.
TXOne Networks Solutions for CVE-2025-31324
The network defense products from TXOne Networks incorporate the updated signature rule for these vulnerabilities to protect your devices from potential attacks. We have also listed the rules below:
| Rule ID | Vulnerability | CVE |
| 1236639 | IWEB SAP NetWeaver Unauthenticated Upload Vulnerability | CVE-2025-31324 |
Indicators of Compromise
- system[.]jsp
- shell[.]jsp
- .properties
Reference
- New Exploit for Critical SAP Vulnerability CVE-2025-31324 Released in the Wild (2025, August 15). https://onapsis.com/blog/new-exploit-for-cve-2025-31324/
- Threat Actors Exploiting CVE-2025-31324 After Public Release of Exploit by ShinyHunters. https://onapsis.com/blog/cve-2025-31324-exploit-update-attacker-analysis/
- SAP Security Note #3594142. https://me.sap.com/notes/3594142
- SAP Security Note #3604119. https://me.sap.com/notes/3604119/E