Feb 26, 2026
Never trust, always verify
Learn more about how TXOne’s OT zero trust approach can help you keep the operation running.

EdgeIPS delivers comprehensive network security tailored for OT. Built on a zero-disruption design principle, it safeguards OT networks while maintaining uptime and performance.
What sets EdgeIPS apart is its Industrial-grade protection, effortless deployment, and deep visibility into assets and vulnerabilities.

Form factors designed to match diverse assets, connections, and environments.
Fast, scalable deployment that minimizes downtime and accelerates security outcomes.
Integrates into existing OT networks without redesigns or specialized expertise.
Automates rule creation from operational patterns, reducing effort and ensuring consistent protection.

Switch between Monitoring and Prevention modes to balance security with operations.
Dual-unit deployment keeps defenses active with automatic backup.
Every EdgeIPS system is built with advanced fail-safe mechanisms, ensuring critical processes stay online regardless of network conditions or disruptions.
With universal bypass and failover support, the EdgeIPS Pro series preserves operational resilience even if connectivity to the uplink switch is compromised.
Purpose-built inspection for industrial protocols prevents disruptions and ensures process continuity.
Flexible Layer 2/3 controls secure both legacy and modern assets across diverse networks.
Driven by TXODI, EdgeIPS continuously interprets traffic across all layers (L2–L7), automatically refining allowlists and blocklists.
Safeguard critical infrastructure from evolving malware, spyware, and content-based attacks.

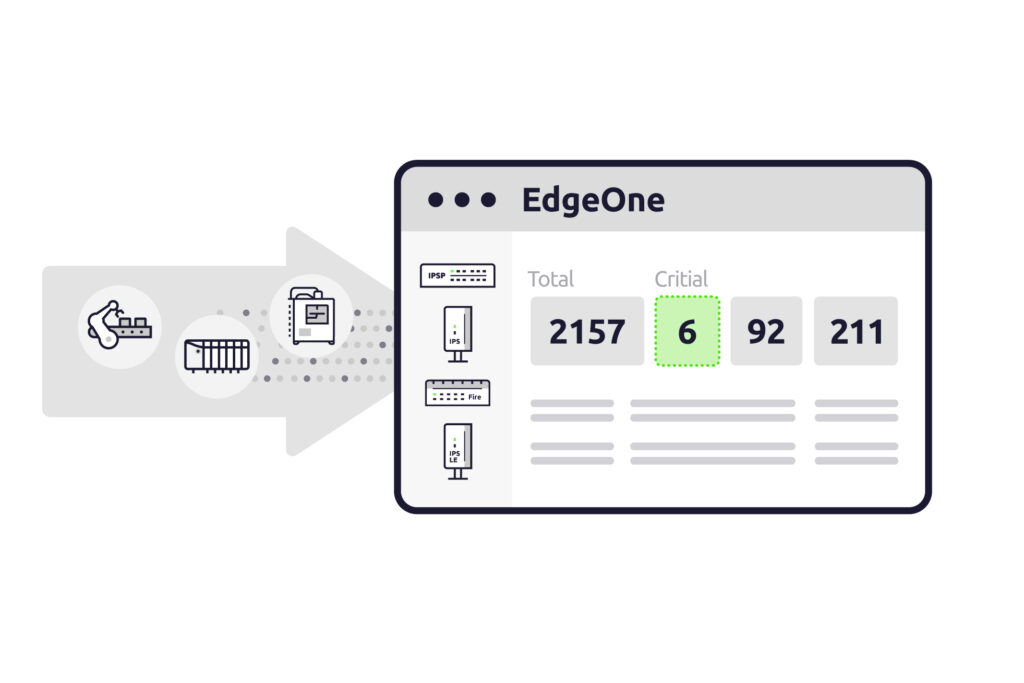
Manage all security appliances from a one intuitive view with unified security controls.
EdgeIPS delivers continuous visibility into bandwidth, application activity, and communication patterns.
From a bird’s-eye view down to individual connection paths, EdgeIPS transforms raw network data into clear context.
Interactive maps reveal how assets interconnect, making it simple to evaluate potential risks and prioritize remediation.

Packet-based detection feeds into the EdgeOne dashboard, turning findings into clear, actionable guidance.
By identifying asset types and operating systems, EdgeIPS highlights the vulnerabilities that matter most.
Risky external connections are flagged instantly, stopping hidden pathways from becoming entry points.
Online and offline update options ensure defenses stay aligned with the latest threats—even in air-gapped environments.

Unify identification, protection, detection, and response into a seamless governance flow that simplifies oversight and reduces complexity.
Continuously monitor security posture to catch risks early, preventing small issues from escalating into costly downtime.
When vulnerabilities arise, EdgeOne turns detection into immediate, actionable mitigation with just a few clicks.
Integrate security with operational insights for coordinated defense across all Edge nodes and TXOne solutions.
 EdgeIPS Pro Series |  EdgeIPS Standard Series |  EdgeIPS LE Series |
We look forward to hearing from you! To send us your questions, fill out this form. A member of the TXOne team will get in touch shortly.
Learn more about how TXOne’s OT zero trust approach can help you keep the operation running.