The Strategic Imperative of Water and Wastewater Systems (WWS)
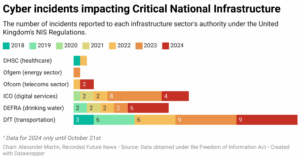
Responsible for everything from potable water to wastewater sanitation, the Water and Wastewater Systems (WWS) sector operates behind the scenes to uphold the function of our modern society. The WWS sector is so critical that any interruption of the service would have a devastating impact on every aspect of a nation. No one can even imagine a world where water service is interrupted. However, the sector’s importance goes far beyond people’s daily lives. Water is a critical component of other sectors as well. Energy plants, firefighters, and other manufacturing facilities all rely on water as an indispensable resource for their operations. However, its vitality as a foundational pillar of society has made it a significant target for sabotage; recently the number of cyberattacks against this sector has increased dramatically. This chart from the UK demonstrates this trend. While in 2018, there were only 2 incidents, the number has tripled by 2024. As a result, authorities such as CISA, have issued an official warning about the Water and Wastewater Sector (WWS) as a target for active exploitation.
A Paradigm Shift
Driven by the need for operational efficiency, regulatory compliance, and the improvement of services, the WWS sector is currently in the midst of a profound transformation. In recent decades, water utilities have integrated a range of technologies into their operations—adopting Information Technology (IT) such as data management and customer billing systems, as well as Operational Technology (OT) like ICS to monitor and control pumps, valves, and chemical dosers. As a result, these water utilities are turning operations that were traditionally manned by human workers into a complex, interconnected cyber-physical system that fundamentally introduces a whole new world of threats. But we’ve barely begun to scratch the surface of just how dangerous these threats can truly be.
The ironclad defense of ‘air gap’ has been dismantled by the convergence of IT and OT; without that barrier, threats are spilling over from IT environments into the highly sensitive OT domain. As more OT systems integrate with IT, the water utilities continue moving away from that isolated and safe OT environment. Thus, many water utilities operate within a digital environment without proper management, creating a pathway for attackers to access OT assets after they successfully compromise the organization’s IT. According to a 2022 report, 83% of water organizations had undocumented or uncontrolled external connections into their OT environments, showcasing the pervasive and detrimental nature of this convergence. Moreover, some water utilities even have internet-facing OT components, allowing the attackers to find and directly exploit OT with ease.
However, water utilities are still anchored in the traditional civil engineering approach which prioritizes aspects like workforce training or budget priorities. A 2021 survey shows that nearly 40% of the WWS respondents do not address security in the overall risk assessment and only 22% have implemented some form of cyber protection. Three years later, in the 2024 State of the Water Industry (SOTWI) report, only half of the utilities surveyed are currently investing in cybersecurity measures to protect their critical infrastructure.
Overview of Water Utility
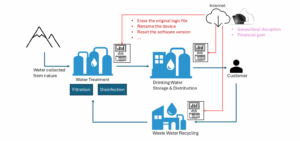
To better understand the threats and impact for WWS, let’s take a look at the process of water utilities. The following diagram illustrates high-level processes; keep in mind that each of these processes has a PLC (programmable logic controller) associated with the operation. For example, a water utility relies on various treatment processes to make water safe for drinking before distributing it to customers. PLCs control both the dosage of required chemicals during treatment and the water pressure for distribution. Most cyberattacks against water utilities aim to compromise these PLCs, manipulating the chemical dosage to dangerous levels or changing the water pressure to disrupt its distribution, causing the water to be cut off. Considering how devastating the impact of this can be, water utilities make attractive targets for motivated threat actors from around the globe. According to our research, there are two major types of threat actors in this sphere.
The Two Faces of Cyber Threats to Water Utilities
Based on past cyber incidents in the WWS sector, the two major motivations for adversaries are a) geopolitical disruption, and b) financial gain. For geopolitical disruption, one notable incident occurred in April 2020, where an Iranian-linked threat group attempted to manipulate the chemical levels at several Israeli water facilities. The attempt was to increase the chlorine concentration used in the water supply. While chlorine is used to purify water to make it safe for consumption, excessive chlorine in water can cause severe issues like nausea, vomiting, and has even been linked to an increased risk of cancer. The attack was detected and thwarted immediately by the authorities before any harm befell the public. However, it still caused a high degree of fear within the public towards water consumption. Fast forward to December 2023, another cyber incident occurred in Ireland, County Mayo, where hundreds of households in this coastal region suffered for two days from a water outage. The attack was conducted by shutting down a controller that helped to maintain water pressure, disrupting the water supply. Though this chaotic event was confined to a small region, it still demonstrates how capable adversaries are of causing serious disruption.
In addition to nation-state threat actors motivated by geopolitical disruption, the WWS sector is also under constant attack from cybercriminals pursuing financial gain. Ransomware groups have learned that disrupting OT environments like threatening the water supply can pressure victims to pay ransoms more quickly. United Kingdom water supplier, Southern Water, was forced to shell out millions due to a Black Basta cyberattack in 2024. While Southern Water claimed that only the IT system was impacted, the mere risk of water supply disruption was dire enough to force the company to pay the ransomware, as revealed by leaked internal chat logs from the Black Basta ransomware gang. Another UK water supplier suffered from a ransomware attack in 2022. In this incident, ransomware gang Cl0p claimed to have compromised South Staffordshire Water, providing proof in the form of two screenshots of the SCADA system used in the operation. While OT operations were not impacted in this incident, the leaked documentation may still increase the risk of future attack.
The Path of Least Resistance: How Adversaries Compromise Water Utilities
Based on the analysis of past incidents, we observed that many attacks were facilitated by internet-exposed OT assets that have default credentials and unpatched systems. This is the most critical pattern found within these incidents. Although these attacks were low in sophistication, they still had a significant impact on the WWS sector. Because water utilities are vulnerable to simpler methods, adversaries have little incentive to use advanced tradecraft. Take Iran’s CyberAv3ngers and pro-Russian hacktivists for example; they constantly scan and exploit internet-exposed PLCs and Human-Machine Interfaces (HMIs) to find default passwords and known vulnerabilities instead of developing and deploying an advanced zero-day exploit.
As an example of the low-effort attack tactics threat actors tend to employ, let’s look at what happened with the Unitronics Vision PLC. This PLC has been used extensively in WWS Sector facilities to control and monitor various stages and processes of water and wastewater treatment. This includes filling tanks and reservoirs by turning on and off pumps at a pump station, flow pacing chemicals (this means injecting or extracting chemicals from the water) to meet regulations, announcing alarms for operations and gathering compliance data for monthly reports. Considering how many functions this PLC is involved with, it was easier for attackers to find the vulnerability of this PLC among the KEV catalog than to build a cyberattack from scratch. The default password of Unitronics Vision series’ PLC was “1111” and the default TCP port was 20256 for communication. When the PLC is exposed to the internet, a threat actor can compromise the device by authenticating to it and using the Unitronics VisiLogic engineering workstation software to tamper with its intended functions. Actions taken by a threat actor after compromise may include:
-
- erasing the original logic file to prevent the device from carrying out its intended operation
- renaming the device to delay OT operators from accessing the device for recovery purposes
- resetting the software version to block communications from engineering workstations
One may think that changing the default password is enough to prevent attacks, but the fact that the PLC is exposed to the internet means the attacker may still be able to exploit a wide range of other vulnerabilities. For example, the same Unitronics Vision™ series PLC is prone to a vulnerability that allows the password to be recovered in plaintext. Water utilities provide 24/7 water service, making it difficult to update the system to patch vulnerabilities. As a result, these PLCs are often at risk of having their known vulnerabilities exploited.
Besides the constant risk that comes from having directly exposed OT assets, attacks that spill over from IT environments are also common. Many water utilities have flat IT and OT boundaries with weak DMZ control, allowing attackers to easily move laterally from IT to OT assets. Another common case in this category are dual-homed assets that have access to both IT and OT. An incident in 2016 provides a notable example. The Kemuri Water Company had a customer-facing web application connected to a server, AS/400, which hosted both billing data and SCADA at the same time. As stated in the above verizon link, “KWC referred to this AS400 system as its ‘SCADA platform’. This system functioned as a router with direct connections into several networks, ran the water district’s valve and flow control application that was responsible for manipulating hundreds of Programmable Logic Controllers (PLCs), housed customer PII and associated billing information, as well as KWC’s financials.” In this incident, the attacker first exploited the web application with an easily identified vulnerability found in the payment application. After the web application was compromised, plaintext credentials were found on the system. Using these credentials, attackers were able to access the control applications used for valve/flow control. According to the report, the attacker managed to alter the amount of chemicals in the water treatment, a terrifying outcome.
The Dilemma of Water Utilities
So why is it so hard to implement effective security practices for water utilities? We found that there are several factors.
-
- Highly fragmented OT assets, very few operators. A water utility is composed of several plant sites, including areas for a storage system and water treatment. Many of these plant sites are small and located in rural areas, and they have a limited budget for OT security personnel. Thus, many remote pump/lift stations operate without any human labor.
- Centralized SCADA supervising covering many small sites. In OT, a master refers to the central SCADA master station that supervises and communicates with multiple RTUs, PLCs, or field devices across distributed sites. If there is only one master, that master can become a single point of failure for a whole service area.
- Aging control assets and long lifecycles. PLCs/RTUs and radios often run 10–25 years; many lack modern authentication, logging, or cryptography.
- Legacy protocols. Modbus is still a common protocol over radio/cellular and OPC UA security is unevenly deployed.
- Tight availability windows. In OT, 24/7 processes with limited bypass options make maintenance windows scarce, leading to routine deferral of patching and firmware updates.
- Remote access dependence. Vendor/contractor access is common; MFA and jump-host discipline are inconsistent.
- Telemetry realities. Licensed/unlicensed radio and cellular links are widely used; shared keys, flat routing, or plaintext protocol tunneling are still seen.
- Less prescriptive cyber compliance. Unlike electric power (NERC CIP) or many oil & gas majors (corporate/IEC 62443 programs with audits), water’s mandates are newer, variable by jurisdiction, and less rigorously enforced, especially for small systems.
To Achieve Better Hygiene
As a response to these escalating cyber threats against water utilities, there are two major frameworks that can be followed:
-
- CISA, EPA and FBI joint direction.
Reduce internet exposure, change default passwords, inventory IT/OT assets, back up systems, conduct regular assessments, train staff, and exercise IR/DR. EPA can supplement this with a 24/7 help desk, free third-party assessments, planning templates, training, and funding pointers (DWSRF/CWSRF; SLCGP). - European Union, NIS2.
NIS2 requires a formal risk-management approach, incident handling, business continuity, and supply-chain security for essential entities—including water. National plans (e.g., ENS/ANSSI/BIO) reinforce risk assessments, monitoring, patching, strong auth/crypto, and DR planning.
- CISA, EPA and FBI joint direction.
Based on the above two frameworks, we conclude the following can be a reference for the minimum baseline for better security hygiene:
-
- Eliminate public internet exposure. Remove direct access to HMIs/PLCs/VPN portals; place access behind authenticated remote entry with MFA; regularly verify that there are no exposed services.
- Identity & credentials mitigation. Change all default credentials and enforce MFA for any remote administrative access. Time-box the vendor accounts and rotate passwords after contractor work.
- Asset & protocol inventory. Maintain an ongoing live register of all servers, workstations, PLCs/RTUs, radios, firmware, and protocols.
- Backups & restore. Keep offline/immutable backups of controller logic and supervisory servers, test recovery, and record results.
- Reduce vulnerability exposure. Plan patch/mitigation cycles; replace end-of-support systems; request CISA free vulnerability scanning and EPA cyber evaluations to catch misconfigurations.
- Plan, train, and exercise. Use EPA’s incident action checklists, IR guides, and tabletop exercise materials, schedule staff awareness training and review phishing hygiene. Record attendance and outcomes to demonstrate due care.
In short, we should generate a prioritized set, execute control actions, and leverage services to keep a concise record for security.