By: Chizuru Toyama, TXOne Threat Research
Executive Summary
- Critical Vulnerability: A trivial authentication bypass (CVE-2026-24061) allows unauthenticated root access on GNU inetutils telnetd.
- Active Exploitation: We have observed three distinct waves of attacks starting Jan 22, 2026, shifting from probing to active weaponization.
- Immediate Action: Restrict access to all Telnet services immediately, as active services are found on both standard and non-standard ports. Update GNU inetutils to a fixed release (versions newer than 2.7).
Overview
CVE‑2026‑24061 is a critical authentication‑bypass vulnerability in GNU inetutils telnetd. During Telnet option negotiation, a remote client can inject environment variables using the NEW‑ENVIRON mechanism (RFC 1572). On vulnerable telnetd versions, the value of USER is forwarded unsanitized to the system login program; setting USER=-f root causes login to treat the session as “pre‑authenticated,” yielding an unauthenticated root shell. Because telnetd directly passes the USER environment variable as an argument to /bin/login, the injected value is interpreted as a command-line option rather than a username.
Public advisories report impact across inetutils 1.9.3 through 2.7, introduced by code changes dating back to 2015, with fixes landing in newer releases. Active exploitation has been observed shortly after disclosure.
Why this matters: Telnet is a legacy, clear‑text protocol, but it still appears in OT/ICS, embedded devices, and long‑lived infrastructure. A trivial pre‑auth root on any exposed Telnet service is high‑impact—even if your “crown jewels” aren’t reachable over port 23.
Internet Exposure
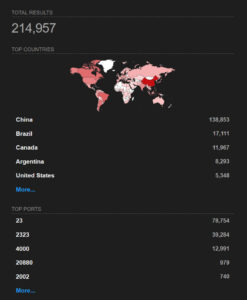
A Shodan search conducted on 2026‑01‑25 using Telnet service identification based on protocol and banner analysis returned over 214,000 internet‑exposed hosts responding as Telnet services. The largest concentrations were observed in China, Brazil, Canada, Argentina, and the United States. Rather than relying on port‑based filtering, this approach captures Telnet services operating across both standard and non‑standard ports, highlighting that legacy Telnet remains widely exposed on the public internet. Although not all identified hosts necessarily run vulnerable versions of GNU telnetd, this level of exposure significantly amplifies the real‑world impact of CVE‑2026‑24061, particularly in environments where Telnet persists for legacy, embedded, or operational reasons.
Our Telemetry
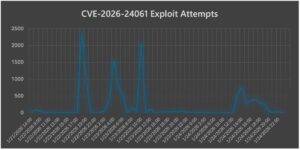
What stands out in our telemetry is not just volume, but a clear, phased operational pattern that mirrors post-disclosure attacker workflows. Our telemetry indicates coordinated but phased exploitation involving 52 distinct source IPs across 16 countries, with clear differences in payload usage by time and geography.
- Inline command payloads were first observed from China and Hong Kong on Jan 22 around 06:00, suggesting early validation or targeted exploitation.
- The first major mass‑scanning peak occurred on Jan 22 around 18:00, originating from an IP in the United States, and primarily used short, probe‑only NEW‑ENVIRON payloads; downloader (.sh) stagers were later observed from the same source, indicating follow‑on exploitation.
- The second peak involved multiple IPs in Japan and the United States, again dominated by short probe payloads, while the third peak was driven primarily by U.S.‑based IPs.
Overall, the progression from probe‑only payloads to inline verification and downloader stagers reflects a typical post‑disclosure workflow of mass discovery followed by selective weaponization.
Payloads Observed (Three Operational Patterns)
Attackers abusing CVE‑2026‑24061 in GNU inetutils telnetd are not using a single, static exploit. Our telemetry captures three distinct payload styles that all begin with Telnet option negotiation and the NEW‑ENVIRON mechanism to inject USER=-f root—the crux of the authentication bypass. Even without any appended commands, a vulnerable system will still drop the attacker into an interactive root shell. (Telnet IAC/WILL/DO/SB/SE per RFC 854; environment variable exchange per RFC 1572.)
1) Probe‑Only: Minimal NEW‑ENVIRON Injection
Purpose: Fast vulnerability validation without immediate post‑exploitation.
What it looks like (abridged):

Why it matters: On vulnerable inetutils telnetd (≤2.7), this can make telnetd invoke login as login -f root, bypassing authentication. Even with no commands appended, the attacker can gain an interactive root shell.
2) Inline Command Execution: Bypass + Immediate Commands
Purpose: Confirm root and proceed quickly.
What it looks like (example):
![]()
Why it matters: The plaintext id immediately verifies that the bypass succeeded (expect uid=0(root) on success) and often precedes further actions (e.g., uname -a, quick file pulls). Public reporting confirms rapid weaponization of CVE‑2026‑24061 and active exploitation soon after disclosure, which aligns with this “confirm‑and‑continue” pattern.
3) Downloader Stager: Bypass + .sh Retrieval (Multi‑Fallback)
Purpose: Reliable post‑exploitation on constrained systems (IoT/OT/embedded).
What it looks like (representative):
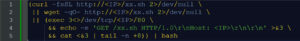
Why it matters: The stager tries curl, then wget, then raw /dev/tcp HTTP to maximize execution success, and pipes directly into bash (memory‑only). This is a common automation pattern in Telnet exploitation waves following disclosure of CVE‑2026‑24061 and has been observed in active campaigns.
Mitigation & Hardening
1) Remove or isolate Telnet
-
- Best: Disable telnetd everywhere; migrate to SSH.
- If you can’t remove it immediately, restrict exposure (IP allow‑lists, jump hosts, VPN segmentation), and block TCP/23 & 2323 at perimeters unless explicitly required.
2) Patch / upgrade
-
- Update to fixed inetutils (reports cite fixes beyond 2.7; check your distro’s backports and changelogs). If upgrades lag, apply vendor patches or backports that sanitize USER before invoking login.
3) Compensating controls
-
- Configure login to reject -f from untrusted callers or enforce — delimiters to stop option parsing where supported.
- WAF/NIDS rules for NEW‑ENVIRON/USER/-f root and for HTTP pulls of known staging paths used by active campaigns.
4) Monitoring & IR
-
- Hunt for recent Telnet logins followed by curl/wget//dev/tcp activity, and for artifacts in /tmp, /var/tmp, /dev/shm.
- If compromise is suspected on embedded/IoT, use re‑imaging or factory reset + latest firmware over ad‑hoc cleanup.
TXOne Networks Solutions for CVE-2026-24061
TXOne Networks’ defense products incorporate updated signature rules for this vulnerability to protect your devices.
| Rule ID | Vulnerability |
| 1237886 | TELNET GNU Inetutils telnetd Remote Authentication Bypass |
References
- RFC 854 — Telnet Protocol Specification [rfc-editor.org]
- RFC 1572 — Telnet Environment Option (NEW‑ENVIRON) [rfc-editor.org]
- NVD entry: CVE‑2026‑24061 [nvd.nist.gov]
- The Hacker News: Critical GNU InetUtils telnetd Flaw Lets Attackers Bypass Login and Gain Root Access [thehackernews.com]
- BleepingComputer: Hackers exploit critical telnetd auth bypass flaw to get root [bleepingcomputer.com]





