By: Chizuru Toyama, TXOne Threat Research
Introduction
In March 2024, the security community was alerted to ShadowRay—the first major campaign targeting AI workloads by exploiting CVE-2023-48022. This vulnerability stems from a missing authentication flaw in the Ray Jobs API, allowing unauthenticated attackers to execute arbitrary code across distributed AI clusters.
Though the initial ShadowRay campaign was serious, our latest telemetry has revealed an even more alarming evolution: ShadowRay 2.0. This is no longer just a niche attack on AI researchers; it has become a “DevOps for cybercrime” operation. Established botnet families—including RondoDox, MooBot, and KmsdBot—have now integrated this two-year-old vulnerability into their automated exploit kits. By leveraging AI-generated payloads and cloud-native orchestration, these actors are transforming high-performance AI infrastructure into self-propagating engines for cryptojacking, DDoS attacks, and data exfiltration.
Observed Payloads and Their Behavior
Example 1: Reconnaissance Payload

Description: This payload performs system reconnaissance by:
- User Enumeration: Reads /etc/passwd to list system accounts.
- Environment Variable Dump: Executes printenv to expose sensitive credentials or tokens.
- Identity Checks: Runs whoami and id to confirm execution context and privileges.
Security Implication:
Attackers use this to map the environment, identify privilege level, and harvest secrets for lateral movement or privilege escalation. Even in the absence of immediate malware, this reconnaissance phase is critical for staging high-impact follow-on attacks.
Example 2: RondoDox Botnet Payload
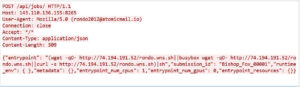
Description: This payload represents a more advanced stage of the attack, focusing on malware delivery and persistence.
- Attacker Signature: The User-Agent field contains the email rondo2012@atomicmail.io, a known signature of the RondoDox botnet operator.
- Infrastructure: Targets rondo.wns.sh, a domain used for hosting malicious shell scripts and C2 communication.
- Resilient Execution: Attempts wget, BusyBox wget, and curl to ensure the malicious script is fetched regardless of available utilities.
- Direct Execution: Pipes the fetched script directly into sh, enabling in‑memory execution without leaving a persistent file initially.
Security Implication: This is a definitive Remote Code Execution (RCE) event. The presence of RondoDox indicates professional botnet operators have fully integrated CVE‑2023‑48022 into their exploit kits.
Example 3: MooBot (Mirai Variant) Recruitment
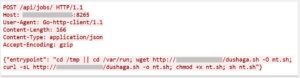
Description: This payload targets the Ray Jobs API to conscript clusters into a DDoS botnet.
- Dual Download Methods: Uses wget and curl -sL to fetch dushaga.sh from the IP which is frequently linked to MooBot.
- Persistence Setup: Saves the script as nt.sh, makes it executable (chmod +x), and runs it immediately (sh nt.sh).
- Threat Actor: MooBot typically weaponizes high-compute environments for massive DDoS attacks.
Security Implication:
This is a classic remote code execution (RCE) pattern designed for initial compromise and deployment of secondary payloads (e.g., cryptominers, botnet agents). By staging in /tmp or /var/run, attackers avoid permission issues and improve odds of successful execution.
Example 4: KmsdBot Malware Injection
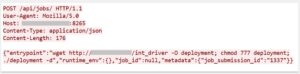
Description: This payload deploys a persistent, compiled binary to hijack high-performance AI compute resources.
- Masquerading: Downloads a file named int_driver and renames it to deployment to blend in with legitimate orchestration logs.
- Daemonization: Executes with the -d flag, ensuring background persistence.
Security Implication:
Activity tied to KmsdBot, a Go-based botnet targeting cloud-native infrastructure for cryptomining and DDoS.
Activity Trends: Monthly Counts
Our telemetry shows that initial exploit attempts appeared as early as April and May 2024, shortly after the ShadowRay campaign disclosure. These early probes were limited and primarily focused on reverse shell execution via the Ray Jobs API, indicating attackers were testing foothold techniques rather than deploying full botnet payloads.
After these sporadic attempts in 2024, activity surged dramatically in Q4 2025, peaking in November:

Q4 2025 total: 803 (45 in October, 386 in November, 372 in December).
This sharp escalation reflects a shift from isolated testing to full-scale weaponization. We observed staggered yet overlapping waves: ShadowRay’s recon-led footholds (Oct–Nov) were followed by RondoDox’s mass deployment (late Nov), then MooBot’s large-scale recruitment (late Dec), with KmsdBot injecting persistent binaries at the end of the month. Net result: CVE‑2023‑48022 has now become fully commoditized across multiple botnet ecosystems targeting the Ray Jobs API.
Defensive Measures
- Restrict API Exposure: Never expose Ray Dashboard or Jobs API to the internet. Enforce authentication (OIDC, mTLS) and IP allowlists.
- Network Controls: Apply strict egress filtering; block unauthorized outbound HTTP. Restrict TCP/8265 to trusted management networks only.
- Detection: Hunt for wget\\sh, curl\\bash, /dev/tcp patterns in job submissions. Deploy Sigma/YARA rules for process anomalies.
- Secrets Management: Remove sensitive data from environment variables; rotate credentials immediately if exposed.
- Runtime Monitoring: Watch out for unexpected cron jobs, systemd units, and abnormal CPU/GPU usage.
Key Takeaways
- AI Frameworks Are the New Front Line: Misconfigured AI frameworks are now prime targets for multi-purpose botnets like RondoDox and KmsdBot.
- Acceleration of Exploitation: Attackers rely on simple yet effective “download-and-execute” payloads to gain footholds in high-compute environments.
- Beyond ShadowRay: Every major botnet family is racing to exploit these gaps, signaling a systemic risk for AI infrastructure.
TXOne Networks Solutions for CVE-2023-48022
TXOne Networks’ defense products incorporate updated signature rules for this vulnerability to protect your devices.
| Rule ID | Vulnerability |
| 1234827 | WEB Anyscale Ray Remote Code Execution |





