What is OT?
Operational Technology (OT) cybersecurity is key to protecting factories, power grids, and water systems from cyber threats. While IT focuses on data, OT cybersecurity ensures that the physical processes behind critical infrastructure, manufacturing, energy, and utilities are safe and reliable.
This guide looks at what makes OT security unique. It explains why a strong IT foundation is important. It also provides leaders with ways to create a practical security program that aligns technical defenses with business goals in an industrial setting.
The Difference Between IT and OT Security
Operational Technology (OT) refers to all the hardware and software that controls physical processing systems. Think of Programmable Logic Controllers (PLCs) operating the valves at a chemical factory, Supervisory Control and Data Acquisition (SCADA) systems watching over a pipeline, or Distributed Control Systems (DCS) coordinating the assembly line at a plant. Such systems are the lifeblood of manufacturing, energy, and utilities, and are designed to keep operations like oil refining or electricity delivery moving along without a hitch.
Information Technology (IT), on the other hand, is all about data management and protection. Think of corporate databases, email servers, or cloud platforms. It focuses on the needs of business users such as accountants or marketers who require private, correct, and available data. OT is all about the availability and integrity of physical processes. Plant operators and engineers are best equipped to maintain these operations.
IT Security is like fortifying a digital fortress: Firewalls, antivirus software, and quick patches to keep compromises out. Systems may often be revised overnight with little to no disruption. In contrast, OT cybersecurity operates in a more intricate environment. Many OT systems rely on legacy PLCs or SCADA setups dating back to the 1980s and 1990s. These systems were installed before today’s cyber threats even existed, so they lack built-in security.
Updating them is risky, with potential downtime that could cost millions and endanger workers. For example, shutting down turbines at a power plant during peak demand could have serious consequences. The stakes are higher in OT. Failures can lead to serious physical consequences, like a downed water treatment plant or a manufacturing error that causes equipment failure. For example, IT secures patient records in hospitals, while OT keeps vital systems like ventilators and HVAC units running. This fundamental difference underpins OT’s cybersecurity goal to focus on operational availability.
IT focuses on data confidentiality and control. In contrast, OT aims for continuous operation. This tension needs to be resolved with teamwork and cooperation. Plant managers, who understand daily operations, should work with the IT department to set priorities. A factory may need 24/7 operations to meet production goals, while IT may push for stricter network controls.
Before any programs are affected, stakeholders must agree on goals. These could include keeping the lights on, ensuring safety, or defining acceptable operational limits. Once these goals are clear, they can implement effective security controls in the plant. This teamwork ensures that security supports the operations team rather than hinders it. A united approach is essential for OT security.
IT as the Bedrock of OT Protection
Merging IT security with OT isn’t a one-size-fits-all approach. IT needs frequent updates, but OT prioritizes stability. For instance, restarting a DCS to apply a patch can disrupt factory output, wasting time and money.
It’s also important to involve operational teams early. This helps ensure that security measures, like workarounds for unpatchable systems, support business goals. These goals might include keeping a refinery running or protecting workers.
A factory often cannot afford downtime, even for a few hours, to replace an old PLC during a patch cycle. We must create a practical security program that considers industrial realities. After all, an IT disruption might delay a report, but an OT issue can halt a production line or trigger a safety event, like a pressure spike in a gas plant. That’s why operational availability is crucial in OT.
However, the foundation of IT must be robust for OT security to exist. A weak IT system, such as an insecure VPN or a vulnerable phishing account, can be a gateway for hackers to breach the OT system. To clarify this, if an attacker gains control of a corporate laptop, they could exploit it to disrupt a factory control system, leading to a halt in production.
OT security is at risk if robust IT practices like access controls and network monitoring are not in place, as IT is often the initial target of an attack. Maintaining a strong IT system for OT security is significant and should not be taken lightly.
Security in OT must balance protection and flexibility. For example, an engineer might need to access a turbine remotely during an emergency. If access is too limited, it can delay important safety actions, like reducing pressure in a gas system. Allowing more access, such as regular remote access for OEM vendors, can enhance operations. Yet, this also raises risks if not managed carefully.
The Colonial Pipeline Incident: A Case Study on OT Security
The Colonial Pipeline incident was the largest cyberattack on U.S. infrastructure to date. DarkSide hackers breached the network, making off with 100GB of stolen data. They also unleashed ransomware that crippled IT systems, including those handling billing and accounting.
To prevent further damage, Colonial Pipeline took the drastic step of shutting down the pipeline. Mandiant, a security firm, teamed up with agencies like the FBI and CISA to launch an investigation.
In a bid to regain control, Colonial Pipeline paid the hackers for a decryption key. This move allowed them to restore operations, which resumed on May 12.
The attack highlighted a critical vulnerability: even if the OT systems (which control pipeline operations) aren’t directly hit, a breach in connected IT networks can still bring industrial operations to a halt. This event became a wake-up call for industries to prioritize OT cybersecurity alongside traditional cybersecurity efforts.
The Impacts of IT-OT Convergence and Integration
IT-OT convergence has changed industries. Real-time data analytics helps optimize production. Engineers can now fix systems from anywhere. But this convergence also opens OT systems to cyber threats.
Connecting factory controls to a corporate network brings risks. Ransomware, malware, and targeted attacks can occur. These threats may disrupt physical processes.
The MITRE framework can assist here by pinpointing risks like open remote access, allowing companies to prioritize defenses such as encrypted connections or ongoing monitoring that block intruders without choking the flow of operations.
The MITRE ATT&CK framework for Industrial Control Systems (ICS) identifies risks and points out tactics like exploiting remote access and manipulating control systems.
The 2019 Norsk Hydro breach is a prime case of ransomware transitioning from IT to OT. It halted aluminum production at several plants, with damage estimated to be over $70 million. The attack began when a trusted customer unknowingly sent a compromised email to a Norsk Hydro employee.
OT Security Challenges and Risks
OT systems encounter unique challenges that make securing them more difficult.
- Legacy/Outdated Systems: Many SCADA, PLC, or DCS, components were built decades ago and have outdated security measures. They also run on obsolete software such as Windows XP or Windows 2000.
- IT/OT Integration Linking IT to OT Networks: This leaves systems vulnerable to threats such as malware that leaps from a corporate laptop to the control systems on a factory floor.
- Remote Access Needs: Many contracts require vendors or engineers to have remote access to the equipment to keep it in working order, which attackers can use as an entry point.
- Operational Limitations: Applying patches to OT systems requires downtime, which could interrupt a critical service. In this case, other forms of protection for unpatched devices must be considered.
These issues make systems more vulnerable to cyberattacks. A hacked PLC could alter a batch of chemicals. This might lead to defective products or dangerous situations. Securing an OT environment is tough, especially while trying to maintain reliable processes.
The Threat Landscape: Notable OT Cyberattacks
A string of recent examples illustrates the increased sophistication of OT threats.
SolarWinds Breach: In 2020, attackers used an IT compromise to strike utility OT systems, highlighting the risk of IT/OT convergence.
2021 Oldsmar Water Plant Attack: One hacker exploited remote access to try to poison the town water supply, posing a risk to public safety and highlighting security weaknesses in remote access controls.
2022 Ukraine Power Grid Attacks: As part of a deliberate geopolitical offensive, OT systems were disrupted, causing a power outage. This demonstrated the strategic value of targeting OT in cyberattacks.
These examples highlight the importance of OT security, which addresses the technical vulnerabilities and the day-to-day realities of keeping operations up and running.
OT Cybersecurity Frameworks and Standards You Need to Know
Standards offer a framework for addressing OT security, but they must also align with business goals, pass audits, and satisfy regulatory requirements.
Key frameworks include:
NIST Cybersecurity Framework (CSF) 2.0
This is a flexible model built around six functions: Govern, Identify, Protect, Detect, Respond, and Recover. This can be adapted to OT environments to address unique risks such as vulnerabilities in legacy systems.
IEC 62443
Offers guidelines and best practices for securing Industrial Automation and Control Systems (IACS), emphasizing techniques such as network segmentation for protecting sensitive assets from attacks.
MITRE ATT&CK for ICS
The MITRE ATT&CK matrix describes how the attacker will act in an OT environment, e.g., exploit remote access or manipulate controls, enabling companies to prioritize defenses.
These frameworks are means, not ends. Security should support operational goals to ensure that a factory hits production targets, and that a utility follows regulations without creating needless friction. Overinvesting in complicated controls can slow operations or deplete resources, while underinvesting leads to vulnerability.
The objective is to calibrate security to match the organization’s risk tolerance and operational goals so that protection adds to efficiency and does not detract from it. For example, a factory could employ IEC 62443 to segment its network to isolate PLCs without disrupting production schedules.
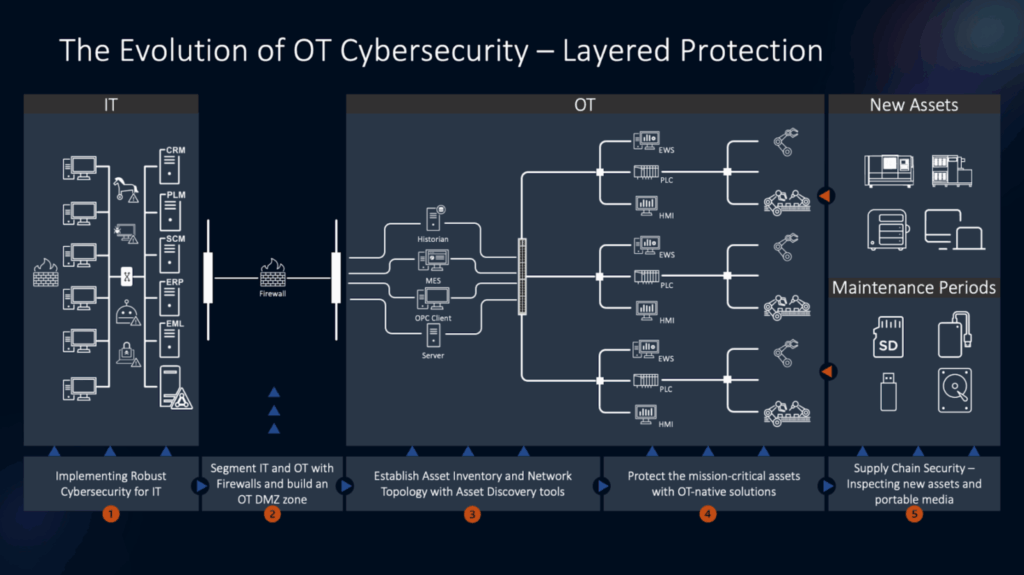
6 Core Practices of an OT Cybersecurity Program
For an effective OT security program that ensures process reliability, reduced operational downtime, and business alignment, these 6 practices should be implemented.
1. Asset-Centric Security
Protect assets effectively by securing each stage of their lifecycle, from onboarding to maintenance. This begins with the onboarding phase, where assets should be scanned and verified as malware-free before being granted entry to the shop floor. The remaining phases of staging, production, and maintenance should be governed by similarly rigorous security protocols.
2. Network Segmentation
Segment OT networks into isolated zones (such as a DCS from IT networks) and conduits for secure communication to limit the spread of an attack. With this, a plant could insulate its production line controls when under attack.
3. Asset Inventory & Passive Discovery
Identify devices such as PLCs or human-machine interfaces (HMIs) and gain visibility into your assets and vulnerabilities with non-intrusive tools that will not influence your operations.
4. Secure Remote Access & MFA
Enable secure remote access for engineers or vendors with encrypted channels and multi-factor authentication (MFA) to balance operational requirements and security. For example, an OEM serving a turbine from afar should utilize a secure gateway.
5. Patches & Compensating Controls for Unpatchables
Leverage industrial firewalls and intrusion prevention systems to protect legacy systems that are not patchable without downtime, allowing operations to continue.
6. Continuous Monitoring & Anomaly Detection
Monitor OT systems in real time to identify unusual activity—such as unauthorized PLC commands—and isolate it immediately, before it affects critical processes. This enables faster response by reducing time spent assessing whether anomalies are actual threats.
OT Components and Their Cybersecurity Implications
These systems have specialized components that all play different roles and have other vulnerabilities. As a result, it’s crucial to secure them for facility and process protection.
HMIs, control refinery, valve levels, and traditional PLCs frequently lack encryption, making them vulnerable to tampering. In 2017, an unsecured Safety Instrumented System (SIS) PLC was targeted in an attack on a petrochemical plant aimed at shutting down operations.
1. Human-Machine Interfaces (HMIs)
These are dashboards that allow human operators to monitor and interact with machines, systems, or processes on the factory floor. An unprotected HMI can transmit misinformation to operators or even send dangerous commands that could jeopardize processes, operators, or equipment.
2. Remote Terminal Units (RTUs)
RTUs, such as those used in pipeline systems, gather data from remote locations and transmit it to central control systems. Their network connection means they can be targeted remotely if they aren’t secured with encryption or access controls.
3. Supervisory Control and Data Acquisition (SCADA) Systems
SCADA systems monitor big operations, such as power grids and industrial plants. Their complexity and IT connectivity have left them vulnerable to malware such as the 2010 Stuxnet worm, which was used to target SCADA to manipulate PLCs controlling nuclear centrifuges.
4. Distributed Control Systems (DCS)
These run and manage automated processes in one location, such as chemical plants or oil refineries. Typically, DCS units of the past cannot be patched without taking them offline, necessitating other defenses such as firewalls.
5. Sensors & Actuators
Sensors monitor conditions like temperature and pressure. Actuators physically manipulate equipment based on this data. When sensors jam, they can send false information. This can harm operations and lead to unsafe conditions.
6. Switches & Routers
These devices interconnect OT networks. Incorrectly configured devices can leave access points exposed. Routers themselves can be exploited for network penetration–as seen in a 2018 attack that compromised hundreds of thousands of home and office routers through known vulnerabilities.
7. Field Devices
These include physical components like valves, pumps, and motors placed throughout a plant. Since they are both network-connected and physically exposed, they are vulnerable to both physical and cyber threats, making them vulnerable areas that need monitoring.
These elements are vulnerable to threats such as unpatched vulnerabilities, remote access attacks, or lack of encryption. For instance, compromised HMI security in a factory may enable an attacker to alter production settings, which can result in faulty products.
Defending these components requires a nuanced, multi-layered approach. Network segmentation can isolate sensitive assets, while anomaly detection can identify threats without disrupting operations. An example of network segmentation is a power plant partitioning its SCADA network to minimize the spread of an attack, thereby preserving the grid’s reliability.
5 Must-Have OT Security Technologies
Organizations need industry-grade technologies to secure OT systems. These solutions tackle OT’s exclusive challenges while meeting operations’ goals.
1. Industrial Firewalls
These serve as a border between IT and OT networks and filter traffic to prevent unauthorized users from entering. A firewall could block malware from reaching a DCS in a factory, thus preserving production uptime.
2. Intrusion Detection Systems/Intrusion Prevention Systems (IDS/IPS)
Intrusion detection systems monitor your network traffic, on the lookout for signs of intrusions, such as abnormal PLC traffic. Intrusion prevention systems are extensions of IDS, able to prevent or block the intrusions that were detected. These are crucial security measures.
3. OT-Aware EDR/XDR & MDR
Combining Endpoint and Extended Detection and Response (EDR/XDR) with Managed Detection and (MDR) offers real-time threat detection specifically for OT. An OT-aware EDR can detect malware on an HMI before it infects half your control room.
4. Secure Data Diodes & One-Way Gateways
These devices allow data to flow only in one direction, preventing outside attacks and threats from entering OT systems. These are perfect for protecting SCADA in utilities, keeping data transmissions secure without impeding operations.
5. Asset Management Platforms
Asset Management Platforms keep track of OT devices like PLCs and RTUs. They provide visibility and vulnerability insights without disrupting operations. A factory can keep an eye on its PLC security to spot vulnerabilities. It can do this while still running production.
These technologies boost OT security. They also support business goals such as uptime and safety. A water utility can use data diodes to keep SCADA systems safe. This helps maintain a steady water supply.
When organizations recognize these priorities, they can use these tools to achieve their newly prioritized goals. This leads to a security program that protects essential functions without causing delays.
Applying NIST CSF 2.0 to OT Environments
The NIST CSF 2.0 Framework is ideal for industries that need to keep factories, power plants, and power grids safe from cyber risks.
- Govern defines roles, risk appetite, and policy. Any further actions must align with these guardrails; otherwise efforts drift, duplicate, or conflict.
- Identify inventories assets, threats, and dependencies. You cannot safeguard, monitor, or restore what you haven’t first catalogued and risk-ranked.
- Protect applies controls that stop many incidents outright. Skipping directly to detection wastes resources on avoidable noise and increases event volume.
- Detect supplies actionable alerts; the Respond function relies on those alerts to isolate and contain threats. Without reliable detection, response teams act blindly or too late.
- Respond stabilizes the environment; only then can the Recover function (the sixth function) safely re-establish normal operations. Rebuilding systems while an attacker is still moving laterally risks reinfection and extended downtime.
Following the prescribed order therefore aligns security work with business priorities (Govern sets the “why” and “how much”) and builds defenses in logical layers (know → prevent → watch → act → restore).
Reordering or merging functions (e.g., lumping Detect, Respond, and Recover together) blurs responsibilities and breaks these dependencies, often leading to gaps, duplicated tooling, and slower incident response time.
Building an OT-Ready SOC
An OT-ready Security Operations Center (SOC) combines IT and OT monitoring to protect industrial systems such as SCADA and PLCs for uninterrupted production. It is designed for manufacturing, utilities, and energy facilities, and combines specialized tools with quick reactions to fight cyber threats.
Visibility
Monitor all OT assets for total visibility of the environment. Imagine a factory that produces maps of HMIs and RTUs with tools such as Cisco Cyber Vision, similar to finding unprotected devices across a network without disrupting production. As a result, blind spots are contained, and teams can evaluate risks, such as exposed sensors, in real time.
Threat Detection
Implement OT-aware tools to identify threats quickly. A utility can deploy EDR/XDR to identify unauthorized SCADA access and sound the alarm before the problem gets out of hand. Passive monitoring tools, such as IDS, observe network traffic and flag anomalies. Example: An energy plant detects rogue PLC commands without shutting down turbines.
Response
React rapidly to isolate incidents while continuing to operate. For example, a refinery might isolate a compromised DCS using predefined response playbooks to minimize disruption. While Security Operations Center (SOC) teams neutralize the threat, OT personnel can ensure uptime. For example, a water plant can shift control systems during a malware attack to keep water flowing while mitigating the incident.
Integrate
Connect IT and OT for better security. For instance, a production SOC can link IT firewalls with OT data diodes. This creates a unified defense. Such teamwork fosters trust, as IT and OT share threat data. It helps stop ransomware from spreading between environments.
An SOC ready for OT operations provides visibility, detects threats, and responds effectively.
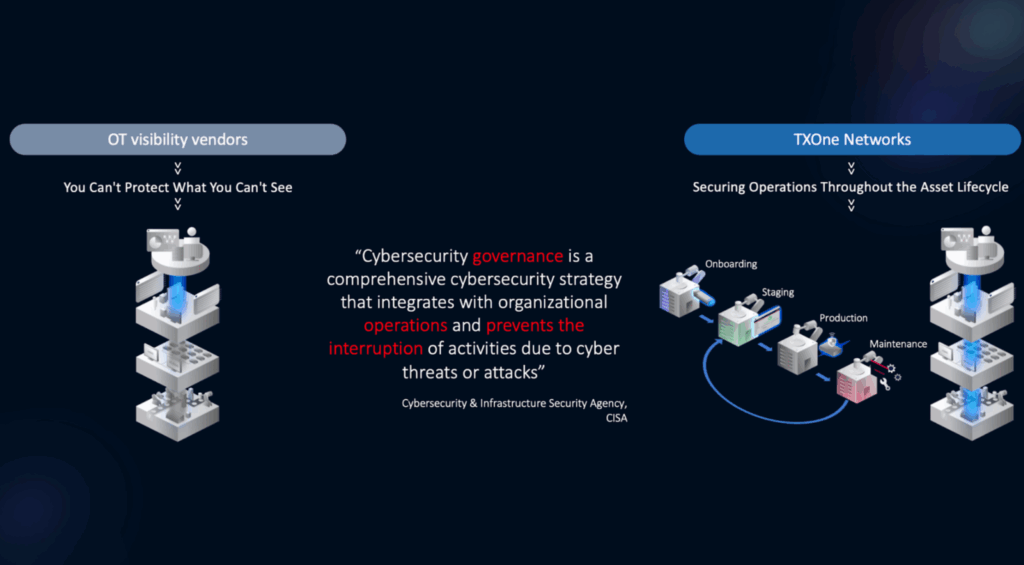
TXOne Provides Asset‑Centric OT Security Across the Industrial Lifecycle
TXOne Networks provides asset-focused OT security, protecting cyber-physical systems across the entire asset lifecycle (onboarding, staging, production, and maintenance) based on its OT zero-trust solution.
Onboarding
Portable Inspector scans laptops, PLCs, and tools before they ever touch the plant’s network, isolating any device that contains malware. Scan reports feed directly into ElementOne for supply chain audit trails.
Staging
During factory acceptance tests, EdgeIPS micro-segmentation blocks unauthorized OT protocol traffic, such as Modbus, enhancing network security. Safe Port is a security inspection kiosk that can sanitize portable media to prevent malware from entering the OT environment. These measures ensure that every workstation meets ISO 27001 / NERC benchmarks prior to deployment.
Production
Stellar OT endpoint protection enforces allowlists and blocks unauthorized changes on HMIs, historians, and engineering stations—preventing ransomware lateral movement while production lines run at full speed.
Maintenance
Pairing Stellar with TXOne SageOne secures aging Windows XP/7 HMIs by enforcing lockdowns, scheduling safe maintenance windows for updates, and quarantining suspicious files—keeping critical legacy assets secure without costly hardware replacements.
TXOne Networks bakes security into every stage of the industrial asset lifecycle. By protecting systems from cyber threats without disrupting operations, TXOne enables your organization to maintain productivity and resilience.
KPIs & Metrics That Prove OT Security ROI
These OT security metrics demonstrate how investments pay off in helping protect factories, power grids, and water treatment systems, while still achieving your organization’s business goals.
Mean Time to Detect (MTTD): Indicates how quickly threats, such as SCADA hacks, are identified after they occur. A utility with the help of TXOne’s EdgeIPS may be able to detect trouble in minutes, not hours. MTTD is calculated by summing the time taken to detect each incident over a given period, then dividing by the total number of incidents. A 15% reduction in MTTD amounts to more alert monitoring and critical time saved.
Mean Time to Respond (MTTR): Measures the average time to respond to a possible security incident, starting from discovery. A factory using TXOne Stellar can stop rogue HMI changes within 40 minutes. This shows how much response latency can be cut down. MTTR is calculated by dividing total response time by the number of incidents. A drop from two hours to under one hour is a huge improvement in production defense.
High-Risk Asset Coverage: Significant systems such as PLCs and DCS units are included in this metric. A refinery, for example, might increase coverage from 65% to 90% of DCS units with EdgeFire. Calculated as: (number of covered high-risk assets ÷ total critical assets) × 100. The higher coverage reduces the attack surface and makes the case for this KPI.
Incident Breakdown: Categorizes threats, such as malware, unauthorized access, or weak configurations by type. Tally incidents by type on a monthly basis to track trends over time. The fewer the attacks, the stronger your defenses are shown to be. Now you are better informed to make relevant business decisions.
Savings Per Blocked Incident: What’s the value? A factory using TXOne’s CPSDR might save $90,000 each time ransomware is stopped. You can estimate your savings by calculating the avoided downtime and cleanup costs per incident.
These numbers tell a story. They show detection speed, response time, asset protection, threat trends, and cost reduction. OT security is valuable. It keeps operations running smoothly and ensures safety.
Future Trends to Watch for in OT Cybersecurity
As cyber threats evolve, so does OT cybersecurity to mitigate risks in industries like energy, manufacturing, and more. Four big shifts we’re witnessing in 2025 include:
- 5G for OT
- AI to spot threats
- Edge-to-cloud convergence
- Post-quantum crypto planning
5G & Private Cellular in OT
5G networks allow robots and sensors to communicate quickly in factories. Soon, factories might swap wires for 5G links. TXOne’s EdgeIPS monitors traffic across protocols such as Modbus. This gives full visibility of the entire network and stops stealthy access. As a result, production remains strong and reliable.
AI/ML Anomaly Detection & Predictive Maintenance
AI hunts for odd behavior and flags gear that needs fixing. For example, a utility could use TXOne SageOne to detect abnormal SCADA signals, while predictive maintenance tools can warn teams about PLC trouble before they disrupt operations. Security measures against AI tampering keep it trustworthy; security and uptime get a lift.
Edge-to-Cloud Convergence
OT often uses the cloud for data access and remote control. With TXOne EdgeFire, firewalls, and MFA, a plant can safely make HMI interfaces available online. This helps teams collaborate more effectively. It’s a safe and practical solution for today’s needs.
Post-Quantum Crypto Planning
Quantum tech could crack old encryption. OT systems, built to last years, need new, quantum-safe codes; a grid might try these on RTUs with TXOne’s zero-trust setup. Starting now follows NIST’s quantum plans; it saves trouble down the road.
These changes build stronger OT security. Rolling out 5G, AI, cloud links, and quantum-ready protection keeps risks low by ensuring that critical systems run smoothly.