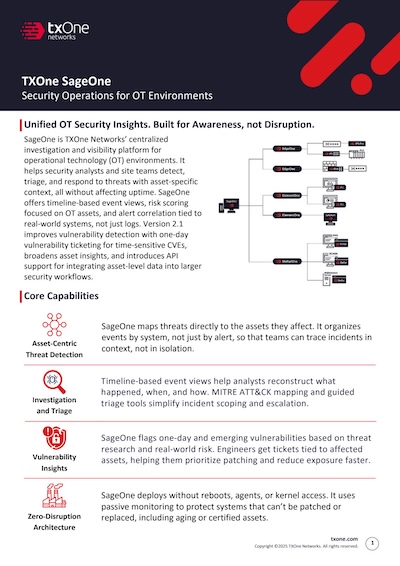
Introduction
Here’s a scenario you might find upsettingly familiar: you’ve got a workstation that’s been functioning reliably for years, managing a critical production line. The system runs custom software that talks to controllers through industrial protocols, and everyone knows not to touch it. Any attempt to update the OS or patch the software runs the risk of breaking everything. At least you have air-gapping to count on, right?
Then one day, someone plugs in a USB drive to transfer a routine recipe update, and that air gap disappears. The aging system couldn’t support modern security software, so there was nothing there to catch the compromise until production ground to a halt as a result of a successful ransomware attack. Now you’re facing ransomware, delayed shipments, and a replacement bill that could hit $2-5 million—plus six months of revalidation and weeks of downtime.[1]
The impossible question becomes: How do we get operations running again and prevent this from happening next time, without replacing systems that have kept production going for decades?
Four Ways Forward
When legacy systems become security liabilities, you’ve got four options. None of them are perfect, and each comes with consequences that extend beyond the technical fix.
1. Keep Running and Hope for the Best
This is the simplest option: change nothing, keep production running, and hope the cyber threats pass you by. It takes minimal effort upfront, but you’re essentially betting that you won’t be the target. As compliance frameworks tighten and attackers get more sophisticated, simply hoping you’re not next becomes less of a strategy and more of a gamble. Also, auditors eventually start asking uncomfortable questions about those unsupported systems. Failed audits lead to remediation plans, which lead to emergency spending anyway—just under worse circumstances.
2. Lock It Down with Network Segmentation
In contrast, network segmentation feels more proactive. At least you’re doing something. You can use VLANs and firewalls to wall off legacy systems from the broader network. This approach reduces exposure, which does matter. But segmentation doesn’t eliminate the vulnerabilities—it just makes them harder to reach. Once an attacker gets inside that segmented zone, whether through social engineering or physical access, the unpatched systems are still defenseless. You’ve built better walls, but once the attacker gets inside, they will still achieve compromise.
3. Replace Everything Under Duress
Sometimes the decision gets made for you. A breach forces immediate action, and suddenly you’re replacing systems in crisis mode. Emergency procurement, expedited timelines, and crisis premiums stack up fast. In automotive plants, where downtime can run over $2 million per hour according to Siemens data, even brief outages create cascading financial impacts.[2] You’re not just paying for new hardware—you’re paying the premium that comes from having no other choice.
4. Extend the Secure Lifespan
There’s a fourth option that often gets overlooked: protect what you already have and extend its secure operation by years. This means applying purpose-built security controls designed for legacy environments—solutions that work without modifying the underlying systems. You can add protection without risking the stability that’s kept those systems running. This path lets you modernize on your own time, not when a crisis forces your hand. And critically, it avoids the multi-million dollar replacement costs while maintaining the operational continuity your production depends on.
What Replacement Really Costs
Equipment replacement carries obvious costs, but the hidden expenses are what often catch teams off guard. The hardware itself runs $2-5 million in many industrial settings. That’s already substantial, but it’s only the most visible line item.
Downtime eats revenue. Every hour offline means lost production. For example, within the automotive sector, one hour of downtime can cost up to $2.3 million dollars.[2] While the line is down for replacement, you’re also missing production targets, delaying deliveries, and creating ripple effects throughout your supply chain. In high-volume manufacturing, those losses accumulate fast. That’s a double blow that impacts both immediate revenue and long-term customer relationships due to reputational loss.
Revalidation takes months, not weeks. In regulated industries, you can’t just swap equipment and resume operations. Pharmaceutical and food manufacturing require full process requalification. Documentation must be updated, testing protocols completed, and regulatory approvals obtained. What looked like a three-week equipment swap at the outset can morph into a six-to-eighteen-month validation project. During that time, portions of your operation remain in downtime limbo.
Expertise doesn’t transfer. The operators who could troubleshoot the legacy system without a second thought will now face unfamiliar interfaces and procedures. New training helps, but it doesn’t replace years of hands-on experience. During the learning curve, you’ll inevitably see higher error rates and slower production speeds. These productivity dips represent real costs even if they don’t appear as separate budget line items.
Emergencies compound everything. When you’re replacing systems because of a security incident rather than planned obsolescence, every cost is amplified. Timelines become compressed, increasing the costs. Lead times that would normally be manageable suddenly become critical path issues. Rush orders, premium freight, and contractor overtime premiums add up quickly.
A More Strategic Path
The reality is that legacy systems don’t have to become liabilities. Strategic life extension avoids replacement entirely by protecting legacy systems for 7-10 additional years without any modifications. Modern OT security solutions are built specifically to protect older environments without requiring system modifications.
To be clear, these aren’t IT security tools that have been reassembled for OT in some hodgepodge configuration. They’re intentionally designed from the ground up for industrial constraints. Constraints such as the fact that systems can’t be rebooted for patches, that available memory is limited, and that any impact on performance is unacceptable. To work around these roadblocks, modern OT strategies pivot accordingly: virtual patching can shield known vulnerabilities without touching the operating system. Application controls can lock down executable processes, preventing unauthorized software from running. Network-level protections inspect industrial protocol traffic and block malicious commands before they reach critical equipment.
Instead of scrambling to replace systems before the next incident, you can plan modernization around scheduled maintenance windows, budget cycles, and operational priorities. Legacy systems can continue running securely while you map out a long-term strategy that makes business sense—not just technical sense.
The cost difference is significant. Where replacement might demand millions immediately, protection strategies typically run in the hundreds of thousands. That gap represents budget that can go toward actual operational improvements rather than emergency mitigation.
Moving Forward
The choice between replacement and protection isn’t just about immediate costs. It’s about who controls your modernization timeline. Crisis-driven replacement puts threat actors in the driver’s seat. Strategic life extension puts you back in control.
Organizations that adopt strategic approaches document $2-5 million in cost avoidance per protected system while gaining 7-10 years to plan modernization according to business priorities. They maintain operational stability, preserve regulatory validation, and protect the institutional knowledge their teams have built.
If you’re facing the million-dollar question with your legacy systems, you have more options than you might think.
Learn the Complete Strategy: Read our comprehensive analysis, Beyond Replacement: Securing What Can’t Be Replaced Through Strategic Life Extension, to explore detailed frameworks for protecting legacy systems, compliance strategies for unsupported systems, and proven approaches from organizations that extended asset life while maintaining security and operational continuity.
Calculate Your Specific Impact: Use our Legacy System Value Calculator to estimate your potential cost avoidance, replacement timeline, and strategic options tailored to your environment. The key is making this decision proactively, while you still have options. Take the power into your own hands—secure your systems, extend the lifecycle of your assets, and be prepared to weather whatever threats might emerge next. Once an incident forces your hand, your options diminish and what’s left behind are far more expensive.
The key is making this decision proactively, while you still have options. Take the power into your own hands—secure your systems, extend the lifecycle of your assets, and be prepared to weather whatever threats might emerge next. Once an incident forces your hand, your options diminish and what’s left behind is far more expensive.
References
[1] Dan Cartmill, “Westlands Advisory Recognizes TXOne Networks as ‘Innovator’ in 2025 OT Cybersecurity Navigator”, TXOne Networks, July 21, 2025.
[2] Siemens, “The True Cost of Downtime 2024”, Siemens, 2024.