Author: Chizuru Toyama, TXOne Threat Research
Background
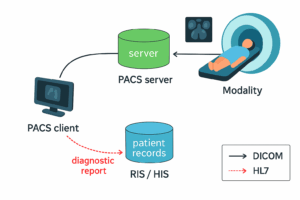
In modern healthcare, PACS (Picture Archiving and Communication System) servers are pivotal—they facilitate the storage, retrieval, and transmission of medical images across healthcare facilities, supporting patient diagnosis and treatment. Any disruption or compromise in PACS infrastructure can imperil patient privacy, workflow continuity, and overall care integrity.
CISA has just published ICS Medical Advisory ICSMA-25-224-01, exposing a set of alarming vulnerabilities in the Santesoft Sante PACS Server (versions earlier than 4.2.3), with a warning of remote exploitation and low attack complexity.
What Is HL7 and Why It Matters
HL7 (Health Level Seven) is an international standard for sharing healthcare information between systems such as Hospital Information Systems (HIS), Radiology Information Systems (RIS), and PACS servers. It acts as a common “language” for exchanging patient demographics, orders, results, and scheduling data.
In a PACS environment, HL7 ensures imaging studies are correctly matched to patient records and updates are reflected across all connected systems. Because HL7 was originally designed without strong security features, flaws in its handling can allow attackers to send crafted messages that disrupt services or compromise sensitive data.
Newly Found Vulnerabilities
| CVE | Vulnerability | CVSSv4 |
| CVE-2025-53948 | Sante PACS Server Double-Free Denial-of-Service Vulnerability | 8.7 |
| CVE-2025-54156 | Sante PACS Server Cleartext Transmission of Sensitive Information Vulnerability | 9.1 |
| CVE-2025-54862 | Sante PACS Server Web Portal Stored Cross-Site Scripting Vulnerability | 4.8 |
| CVE-2025-54759 | Sante PACS Server Stored Cross-Site Scripting Vulnerability | 5.1 |
Successful exploitation of these vulnerabilities could allow an attacker to cause a denial-of-service condition, obtain sensitive information, and steal a user’s cookie information.
CVE-2025-53948 is a vulnerability in the Sante PACS Server related to HL7 message handling. When multiple HL7 packets with non-sequential frame numbers are received, memory management errors may occur, potentially leading to a double free. Exploitation could disrupt PACS services through denial-of-service or create opportunities for further compromise, highlighting the importance of stricter validation and monitoring of HL7 communications.
CVE-2025-54759 is a stored cross-site scripting (XSS) vulnerability that can be triggered through a crafted HL7 message. By injecting malicious payloads into HL7 fields, an attacker may cause scripts to be rendered within the PACS server’s user interface. This could lead to unauthorized actions, data manipulation, or disruption of workflows directly on the PACS system, without requiring a web browser.
Mitigations
To protect against these vulnerabilities, healthcare providers should implement the following measures:
- Upgrade to Sante PACS Server Version 4.2.3 or later.
- Encrypt HL7 and credential transmissions via TLS or VPN tunnels.
- Validate all incoming HL7 messages to reject malformed or unexpected data.
- Monitor PACS logs for unusual HL7 activity.
The network products from TXOne Networks incorporate the updated signature rules for these vulnerabilities to protect your devices from potential attacks. We have also listed the rules below:
| Rule ID | Vulnerability | CVE |
| 1236633 | ICS Sante PACS Server Cleartext Transmission of Credentials Information Disclosure Vulnerability | CVE-2025-54156 |
| 1237180 | ICS Sante PACS Server Stored Cross-Site Scripting Vulnerability | CVE-2025-54759 |
Conclusion
The presence of vulnerabilities in HL7 communication underscores the critical importance of securing healthcare data exchanges. Since HL7 serves as the backbone for connecting HIS, RIS, and PACS, weaknesses in its implementation could expose sensitive patient records and disrupt clinical workflows. By prioritizing HL7 security through network segmentation, message validation, and encryption, healthcare providers can strengthen trust, protect patient data, and ensure the reliability of their interconnected medical systems.
Reference
Cybersecurity & Infrastructure Security Agency. (2025, August 12). ICS Medical Advisory | ICSMA-25-224-01: Santesoft Sante PACS Server, https://www.cisa.gov/news-events/ics-medical-advisories/icsma-25-224-01