Background
The power industry generally refers to electric power generation, transmission, distribution, and retail sectors. To promote renewable energy development and increase energy efficiency, countries such as the European Union, the United States, and China are actively developing Smart grids. The global smart grid market is expected to exceed $50 billion in 2025 [1]. The following figure shows an overview of the power industry ecosystem combined with the smart grid, which can be divided into three categories; power generation, power management, and power retail:
1. Power Generation: As shown in the green area, power generation suppliers include not only integrated manufacturers with electric power generation, transmission, and distribution, but also Independent Power Producers (IPPs). These suppliers generate electricity in the form of thermal, hydro, wind and solar power. When the power generation operator generates electricity, it can first transfer the electricity to the substation through the electric power transmission system, and once it has been analyzed, consolidated and distributed, the electricity is finally sold to the user. Since the addition of renewable energy to the smart grid in recent years, solar energy and wind power generation now have the highest production capacity of renewable energy applications [2]. Solar and wind power generation apparatuses occupy large areas and are often located in sparsely populated areas, requiring the use of IoT technology to function across the grid. Unfortunately, this exposes sensors, controllers, actuators, and inverters that are directly or indirectly connected to the Internet to the risk of cyber attacks.
2. Power Management: As shown in the yellow area, when the power generation company produces electricity, it must manage and distribute electricity through the power grid system. The process will go through one or more substations to decrease the electricity according to different end users. For example, residential electricity may need to be stepped down three times to meet the distribution requirements. The substation is similar to a traditional ICS environment. Its composition includes HMI, IED, field devices, and other devices. The substation also uses Time-Sync equipment due to the need to accurately record the time sequence of events in the grid system so that it can synchronize voltage and current vectors. In conjunction with the development of the smart grid, power companies will also conduct extensive data analysis on the data of the power distribution process to improve operational efficiency. Combining the above-connected features, attackers will have more opportunities to remotely execute attacks on the power management in an ICS environment.
3. Electricity Retailing: As shown in the blue area, after the electricity grid operators have purchased electricity, they will sell it to the public. With the rise of smart factories, smart homes, and electric vehicles (EVs), advanced metering infrastructure (AMI) can achieve real-time power monitoring, scheduling, and distribution through smart meters that can be checked on the internet. Because AMI’s endpoint devices are primarily installed in any accessible geographical location and contain many network nodes, attackers have the opportunity to interfere with the connection between the endpoint device and the Utility Center in an unattended environment. This also affords them the possibility of sending fake data or blocking a connection.
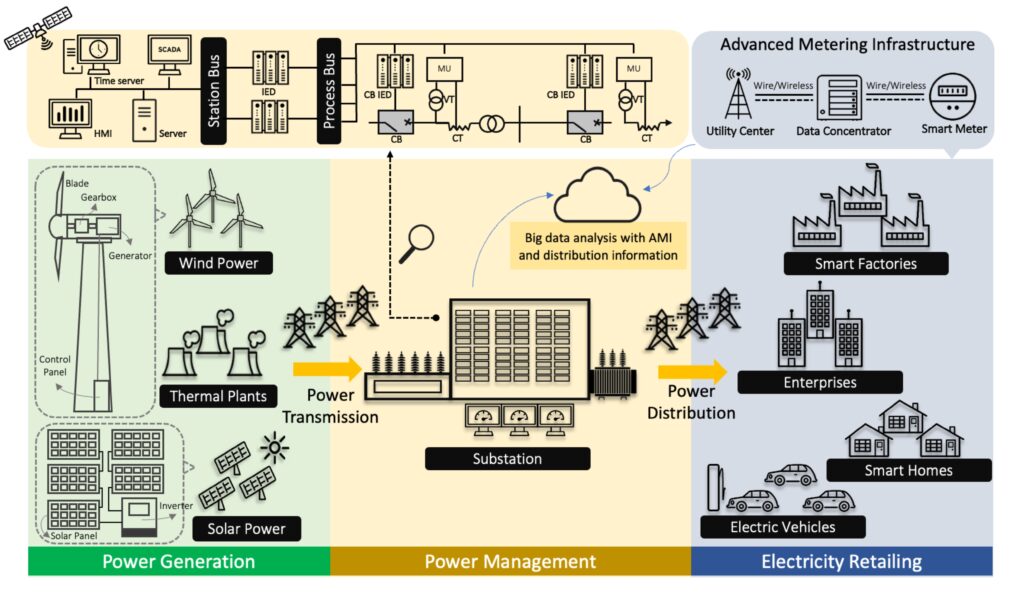
Figure 1. Power Industry Ecosystem Overview
Threats Faced by the Power Industry
Whether it is power production, power management, or power sales, any stage of a cyber attack can result in insufficient power supply to customers, whether they be power companies or residents. Should a power company that distributes electricity be attacked without a contingency plan, it could cause damage to the national economy and even threaten the survival of the people. For example, in December 2015 and 2016, Ukraine’s substations were attacked by malware such as BlackEnergy3 and Industroyer, which forced the public into a long-term power outage throughout the winter. In 2022, the more sophisticated Industroyer2 malware also attempted to attack Ukrainian substations. Fortunately, quick responses prevented the disaster from spreading further [4]. Moreover, in 2021 and 2022, India’s Load Despatch Centers, subsidiaries of the organization that coordinates all power stations in India, also suffered from APT attacks. Although the attacker did not successfully destroy the ICS network in this incident, there was evidence indicating that future attackers might aim to disrupt both power transmission and distribution within the grid [5]. With this in mind, TXOne Networks analyzed the power industry ecosystem and identified the following potential threats:
1. Renewable energy generation facilities are located in unmanageable geographic locations, increasing the chances of attackers gaining access to physical equipment
In terms of renewable energy sources that utilize changes in the physical environment to generate electricity, most of them require the construction of generator sets in specific geographic locations.
For example, when it comes to wind power generation, in addition to the blade, gearbox, and generator, the internal components of the wind turbine also include networked controllers and switches in the control panel (as shown in the green Wind Power area) [6] [7][8]. According to researchers at the University of Tulsa, an attacker can unlock an unsupervised turbine door within a minute and gain network access to every connected wind turbine [9]. Suppose that access control management for privileged accounts is not adequately deployed on the wind turbine system. In this case, many facilities will face the threat of being controlled by bad actors, thereby rendering the power plant unable to generate electricity.
On the other hand, solar power generation units also have a caveat: they need to be placed in an outside setting. This makes the solar panel’s components easily accessible to the attacker, components which include inverters connected to the network (the green Solar Power area in the figure) to supply the power plant. Inverters are connected to the network because there are benefits that stem from communication between the controller (PPC) and SCADA systems [10][11][12][13]. Inverters serve as interfaces between the solar panel and the power grid, which provide functions such as changing the power transmission schedule, shutting down power, and more. In a highly networked power generation environment, if there is no adequate network segmentation between inverters, attackers could destroy one group of inverters and connect to inverters in other areas through it, which may lead to a large number of interrupted events in the generator [14].
2. The lack of security in network protocols used for power generation and management allows man-in-the-middle and spoofing attacks to take place in power plants and substations
IEC 62351 is a cybersecurity standard proposed by the International Electrotechnical Commission for smart grids. Other smart grid-related standards also include automation systems of substations (IEC 61850), communication between substation systems for control message transmission protocol (IEC 60870-5, DNP3), and communication protocol between control centers (IEC 60870-6 TASE.2 ICCP). It supports MMS, GOOSE, SMV, SNTP, and IEEE1588 communication protocols for internal substations adopting the IEC 61850 standard.
In terms of application, the Station Bus area of the substation (the upper part of the yellow area in Figure 1) would use MMS, GOOSE, or SNTP protocol to collect information closest to real-time and complete low-latency network communication. On the other side, the Process Bus adopts SMV, GOOSE, or IEEE1588 communication protocol to provide the connection between IEDs and endpoint devices.
Due to the low latency requirements of the IEC 61850 standard, it is not easy to implement data encryption measures. For example, the maximum delay requirement of the GOOSE protocol is 4ms. If power suppliers want to implement encryption within 4ms, they need to install a high-performance CPU in the IED, which requires redesigning the entire hardware device. In the case of unencrypted data, attackers have the opportunity here to perform man-in-the-middle, spoofing, or other attacks and make the power distribution of substations fail [15][16].
In addition, industrial control protocols for power plants may lack encryption mechanisms for high-speed transmissions, which gives attackers the ability to execute the protocol communications attacks mentioned above. For example, the Ethernet Global Data (EGD) protocol developed by General Electric (GE) is commonly used in power plants such as ones powered by gas turbines. EGD is a UDP protocol using an Ethernet interface that provides fast data exchange for PLCs, drive systems, HMI, SCADA, and other devices. Since the protocol has no associated encryption or authentication mechanisms, an attacker can efficiently perform man-in-the-middle or spoofing attacks when they gain access to a power plant’s network.
3. Power management relies on the GNSS clock as one of their time reference sources, so GPS Spoofing may cause grid supply, demand, or frequency anomalies, leading to increased risk of outages
Since power grids require sub-microsecond accuracy to operate, low-cost, high-accuracy GNSS signals have been implemented for time synchronization. GNSS signals may be generally affected by natural changes such as weather or space environment. However, attackers also have the opportunity to interfere with higher power signals, causing grid failure due to unsuccessful time synchronization, thereby resulting in power outages [17][18]. For example, the Phasor Measurement Unit (PMU) is the most critical device for the smart grid to provide synchronized voltage and current vectors. It uses GPS in order to carry out a high-precision time synchronization. Attackers can perform GPS spoofing attacks on such devices via software-defined radios. If the compromised PMU relays the wrong time, it will lead to phase angle error, creating abnormalities in the grid supply and demand or frequency, which can then lead to power outages [19].
4. Electricity sales use many networked devices. Along with falsifying power data over the network, attackers can even take control of endpoint devices
AMI is an intermediary system between smart grid users and utility companies, mainly including electricity pricing and demand management. Typical components of AMI include a smart meter, data concentrator, utility center, and two-way communication over the network. The smart meter can transmit the user’s power usage data outside the utility center via the data concentrator. The utility center can also transmit control commands to the smart meter via the data concentrator. To cover the distance between devices, AMI often uses wireless technology in data transmission, and attackers can forge power data through corresponding RF tools and thus gain control of endpoint devices [3][20]. Taking EVs as an example, researchers discovered in 2022 that the Combined Charging System (one of the typical fast charging technologies) is vulnerable to disrupting attacks. Through this vulnerability, an attacker could disrupt the charging service of an EV charging station through a wireless signal. If multiple charging stations are terminated without warning, the voltage can become unstable and affect the entire grid [21][22].
5. ICS equipment in the energy industry has a large number of remote, low-complexity, and high-risk vulnerabilities, making effective protection of related components, such as equipment and applications in the power field, a significant challenge
TXOne Networks researchers analyzed ICS vulnerabilities and found that out of a total of 5,254 disclosed vulnerabilities, up to 2,417 have the capability of affecting the energy industry. (As of ICS-CERT Advisory September 25, 2022). Of these, 1,714 vulnerabilities were rated high risk or higher in CVSS v3, meaning that if an attacker successfully exploited this vulnerability, there would be a way to cause a severe availability, integrity, or confidentiality impact on the ICS environment. Among these high-risk vulnerabilities, 1,330 were both remote and low-complexity vulnerabilities, meaning that even less sophisticated hackers could exploit them. Alarmingly, another 95 had their exploits fully disclosed on the Internet, demonstrating the need for the utility industry to protect its ICS equipment. After further analysis by researchers, the highest proportion of these vulnerabilities includes CWE-787 (Out-of-bounds Write), CWE-119 (Improper Restriction of Operations within the Bounds of a Memory Buffer), and CWE-20 (Improper Input Validation). In addition to most devices executing unauthenticated and unverified commands, incorrect buffer limits can prevent device services and even allow malicious programs to be executed. For example, the Emerson Ovation OCR400 Controller, often used in Power Generation, has been found to have an Out-of-bounds Write flaw. Attackers can exploit the third-party FTP service vulnerability embedded in the controller to cause damage to the controller’s memory and allow remote access, thereby allowing the attacker to execute malicious programs on the terminal. In ABB eSOMS (Operation Management System for Power Generation Industry), an Importer Input Validation vulnerability was also discovered, allowing users without proper authentication to upload and execute malicious programs [23][24].
How to Mitigate Potential Threats to the Power Industry
Based on the above threat analysis, we can conclude that, in the power industry–whether in production or sales–many endpoint devices can access the Internet, have a wide range, and communicate closely with substations, making their industrial control environment more vulnerable. Due to the low latency requirements of substations, it is difficult for communication protocols to implement complete security measures. Thus, TXOne Networks recommends the following solutions based on OT zero trust to mitigate potential threats to substations:
1. Portable Security for Detecting Compromised Field Devices:
The initial attack may come from the equipment supplier before the power station equipment has entered the plant facility, so electricity power operators should scan each asset entering the plant facility for malware and establish a health record of it to ensure that the equipment does not contain malware or critical vulnerabilities. To mitigate supply chain attacks, the Trend Micro Portable Security 3 Pro can be used to automatically scan malware, vulnerabilities, and system configuration without connecting to a network. Leveraging the Trend Micro Portable Security 3 Pro allows asset owners to avoid warranty violations and detect malware without changing sophisticated equipment. This will help the power plant to ensure the integrity of the device while complying with the regulatory compliance of the specific industry, such as IEC 62443, NISTIR 7628.
2. Network Defense for Substation Automation System with Station Bus and Process Bus:
Network Zero Trust can use network isolation, optimized network access control, and better intrusion detection analysis to prevent a compromised station bus asset and process bus asset from evolving into a large-scale disaster. To simplify monitoring, restrict hackers’ movement around the OT network, and make it harder for hackers to gather information, TXOne Networks recommends deploying EdgeIPS or EdgeFire on the OT network:
1) Network Segmentation: EdgeIPS or EdgeFire installed inline in protection mode will learn the regular operational traffic. Suppose the perimeter network control is loose, allowing access to a PLC from the Internet. In that case, the EdgeIPS sitting next to the station equipment in the production cabinet would block abnormal connections from the Internet and prohibit the upload of compromised station equipment configuration files to the attacked station equipment.
2) Network trust list: EdgeIPS or EdgeFire supports various industrial control network communication protocols (such as MODBUS, Ethernet/IP, Profibus, and so on) and an in-depth analysis of L2-L7 network traffic that can provide communication protocol command editing at a terminal. Click the operation of the connection to establish an allowed list of network rules. In addition, with network segmentation, all hardware protection devices can be managed visually through the central control platform to reduce risks with the concept of least privilege.
3) Virtual patching technology: EdgeIPS or EdgeFire has a specially designed network policy for packet filtering, designed to resist attacks that exploit known vulnerabilities of communication protocols without forcing endpoints to update the system, which means there is no need to restart the power system. There is also no need to stop the power system to use this technology.
3. Endpoint Protection for Substation Automation Systems with Station Bus and Process Bus:
The device software activation phase requires system hardening methods to eliminate or reduce the means of attack entry, including deploying antivirus software, turning off unnecessary software services, disabling high-risk network protocols, restricting user permissions, and managing physical ports (such as USB access). Through asset security hardening, technicians can significantly reduce the chances of attackers gaining access to critical systems and prevent malicious programs from running. For example, suppose the station bus and process bus equipment run the Stellar agent. In that case, the ICS package can be locked into changes, so that the exploited vulnerability would not be able to drop files or inject new data into the existing files within the package. Behavior monitoring and abnormal behavior prevention would also block the abnormal use of resident system tools, preventing further lateral movement from the compromised power system.
Reference
[1] Bruna Alves, “Smart grids in the U.S. – statistics & facts”, Statista, Apr 8 2022, Accessed Sep 23 2022
[2] International Energy Agency, “Renewable Energy Market Update”, International Energy Agency, May 2022, Accessed Sep 23 2022
[3] Mostafa Shokry, Ali Ismail Awad, Mahmoud Khaled Abd-Ellah, Ashraf A.M. Khalaf, “Systematic survey of advanced metering infrastructure security: Vulnerabilities, attacks, countermeasures, and future vision”, ScienceDirect, Nov 2022, Accessed Sep 23 2022
[4] ESET Research, “Industroyer2: Industroyer reloaded”, WeLiveSecurity, Apr 12 2022, Accessed Sep 24 2022
[5] Security Boulevard, “Cyber Attacks on the Power Grid”, Security Boulevard, May 19 2022, Accessed Sep 24 2022
[6] Lantech Communications Global, “Wind Power Monitoring”, Lantech Communications Global, Accessed Sep 23 2022
[7] Beckhoff, “Wind farm networking with EtherCAT”, Beckhoff, Accessed Sep 23 2022
[8] Yokogawa, “Wind Power”, Yokogawa, Accessed Sep 24 2022
[9] Jason Staggs, David Ferlemann, Sujeet Shenoi, “Wind farm security: Attack surface, targets, scenarios and mitigation”, ResearchGate, Mar 2017, Accessed Sep 23 2022
[10] Tom Kuster, “The future of cybersecurity: How renewable power plant controls protect inverters from hacks and attacks”, Solar Power Installation, Mar 23 2021, Accessed Sep 23 2022
[11] Moxa Case Study, “Solar Power Plant Monitoring and Control System”, Moxa, Accessed Sep 23 2022
[12] TMEIC News, “TMEIC to Supply SOLAR WARE STATION™ and Power Plant Controllers for a Large PV Plant Currently Under Construction in Vietnam”, TMEIC, Accessed Sep 23 2022
[13] Inverter.com, “What is the String Solar Inverter?”, Inverter.com, Apr 1 2020, Accessed Sep 24 2022
[14] TXOne Networks White Papers, “Cyber Safe Green Energy”, TXOne Networks, May 9 2022, Accessed Sep 23 2022
[15] Juan Hoyos, Mark Dehus, Timthy X Brown, “Exploiting the GOOSE Protocol: A Practical Attack on Cyber-infrastructure”, UTC America Latina, Dec 2021, Accessed Sep 23 2022
[16] INCIBE, “Security in the GOOSE protocol”, INCIBE-CERT, Aug 6 2020, Accessed Sep 26 2022
[17] FURUNO Case Studies, “Smart grid and GPS/GNSS timing solutions”, FURUNO, Accessed Sep 23 2022
[18] GPSPATRON Articles, “The Power Grid’s Vulnerability to GPS Spoofing Attacks”, GPSPATRON, Apr 23 2019, Accessed Sep 23 2022
[19] Veerapandiyan Veerasamy, Kalaivani R, Vidhya Sagar Devendran, “Optimal Placement of PMU in smart grid”, ResearchGate, Apr 2017, Accessed Sep 23 2022
[20] Elias Bou-Harb, Claude Fachkha, Makan Pourzandi, Mourad Debbabi, Chadi Assi, “Communication Security for Smart Grid Distribution Networks”, ResearchGate, Jan 2013, Accessed Sep 23 2022
[21] Sebastian Köhler, Richard Baker, Martin Strohmeier, and Ivan Martinovic, “Vulnerability in the Combined Charging System for Electric Vehicles” Brokenwire, Accessed Sep 23 2022
[22] TXOne Networks Blog, “Superfast EV Chargers Used to Hack Power Grids”, TXOne Networks, Sep 12 2022, Accessed Sep 23 2022
[23] ICS-CERT Advisories, “Emerson Ovation OCR400 Controller”, CISA, May 28 2019, Accessed Sep 26 2022
[24] ICS-CERT Advisories, “Hitachi ABB Power Grids eSOMS Telerik”, CISA, Mar 18 2021, Accessed Sep 26 2022





