LockBit Ransomware Analysis
Since its emergence in July 2022, LockBit 3.0 (also known as LockBit Black) has become one of the most notorious ransomware threats worldwide. Several industries have been adversely impacted by LockBit3.0, with numerous semiconductor firms in Taiwan falling victim to its ransom demands.
At this point, LockBit3.0 not only maintains its RaaS (Ransomware as a Service) platform operations, but also steadily enhances its encryption capabilities with various techniques, particularly those focused on anti-analysis.
LockBit 3.0 ransomware requires a password to unpack the original text section, a technique similarly employed by Egregor and BlackCat. Based on code similarities, many researchers assert that the majority of the techniques utilized by LockBit3.0 are derived from BlackMatter/Darkside.
 Figure 1. The entry points of LockBit3.0 (Left) and BlackMatter (Right) are very similar
Figure 1. The entry points of LockBit3.0 (Left) and BlackMatter (Right) are very similar
 Figure 2. The ParseApiHashTable functions of LockBit3.0 (Left) and BlackMatter (Right) follow the same operations
Figure 2. The ParseApiHashTable functions of LockBit3.0 (Left) and BlackMatter (Right) follow the same operations
Utilizing its configuration file, the threat actor can tailor the encryptor for a more adaptable range of options, including customizing the list of terminated services/processes, ransom note, files and folders whitelist, and more.
In this LockBit 3.0 analysis, we examined the sample (sha256: 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce) and highlighted the most prominent techniques employed by LockBit3.0.
 Figure 3. The computer held ransom by LockBit3.0 will have its wallpaper changed, and the icon of the encrypted file will be replaced with Lockbit’s
Figure 3. The computer held ransom by LockBit3.0 will have its wallpaper changed, and the icon of the encrypted file will be replaced with Lockbit’s
 Figure 4. Using this script [1], the configuration can be dumped from the sample –Part 1
Figure 4. Using this script [1], the configuration can be dumped from the sample –Part 1
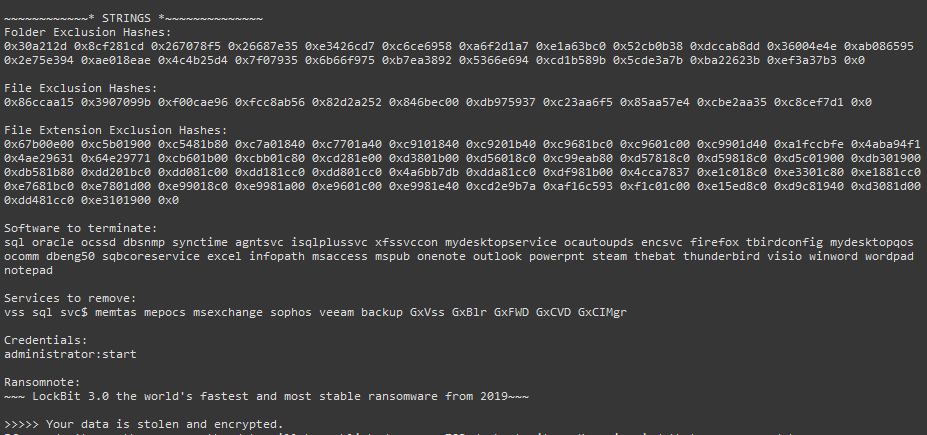 Figure 5. Using this script [1], the configuration can be dumped from the sample – Part 2
Figure 5. Using this script [1], the configuration can be dumped from the sample – Part 2
LockBit 3.0 Analysis: Code Flow
The analyzed sample can be broken down into four distinct phases: Unpack Sections, Reconstruct IAT, Escalate Privilege, and Ransom Main.
1. In the Unpack Sections phase, the actual sections are decrypted.
2. The Reconstruct IAT phase not only restores the functionality of the IAT but also obfuscates the address using a customized stub.
3. During the Escalate Privilege phase, the sample attempts to evolve by granting itself higher privileges.
4. The Ransom Main phase is the most complex stage. Most functions are initiated as child threads, and operations corresponding to the decrypted configuration from the Escalate Privilege phase are executed.
 Figure 6. The code flow of LockBit 3.0
Figure 6. The code flow of LockBit 3.0
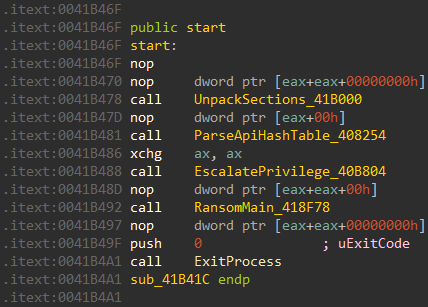 Figure 7. The analyzed sample consists of 4 steps
Figure 7. The analyzed sample consists of 4 steps
9 MITRE ATT&CK Tactics and Techniques for LockBit Ransomware Protection
Initially, we employ the MITRE ATT&CK Tactics and Techniques framework to meticulously examine the LockBit3.0 attack methodology. Following this comprehensive analysis, we delve into the distinctive aspects of the method, enabling readers to gain a thorough understanding of how to dissect these specialized techniques:
Table 1. MITRE ATT&CK Tactics and Techniques
| MITRE Tactics | MITRE Techniques | Description |
| Execution | T1106 Native API | LockBit3.0 adopts Native Windows API |
| T1047 WMI | LockBit3.0 deletes shadow copies through WMI> | |
| Persistence | T1547.001 Registry Run Keys | LockBit3.0 sets autorun registry in the safeboot mode |
| Privilege Escalation | T1134.001 Token Impersonation | LockBit3.0 attempts to impersonate other processes by duplicating their tokens |
| T1548.002 Bypass User Account Control | LockBit3.0 adopts “CMSTPLUA UAC Bypass” techniques to bypass UAC | |
| Defense Evasion | T1140 Deobfuscate/Decode Files or Information | LockBit3.0 requires password to decrypt the sections |
| T1562.001 Impair Defenses: Disable or Modify Tools | LockBit3.0 disables Windows Defender to evade detection | |
| T1070.001 Indicator Removal: Clear Windows Event Logs | LockBit3.0 disables Windows Event Logs to evade detection | |
| T1027 Obfuscated Files or Information | LockBit3.0 obfuscates stack string to make analysis more difficult | |
| T1027.007 Dynamic API Resolution | LockBit3.0 resolves APIs dynamically by comparing the customized hash and modifying the stub in the IAT to make analysis more difficult | |
| T1622 Debugger Evasion | LockBit3.0 adopts multiple anti-debug techniques to make analysis more difficult | |
| T1112 Modify Registry | LockBit3.0 modifies multiple registries (for example, it customizes the desktop by changing the wallpaper and icons) | |
| Discovery | T1614.001 System Location Discovery: System Language Discovery | LockBit3.0 detects language settings to determine whether to execute or not |
| Lateral Movement | T1570 Lateral Tool Transfer | LockBit3.0 laterally moves to other computers through Admin Shares or Domain Group Policy |
| Impact | T1486 Data Encrypted for Impact | LockBit3.0 encrypts all the targeted files |
| T1490 Inhibit System Recover | LockBit3.0 deletes shadow copies to prevent victims from recovering the encrypted files | |
| T1489 Service Stop | LockBit3.0 stops the processes and services listed in the hardcoded configuration |
1. T1140 Deobfuscate and Decode Files or Information
- A stub, situated in the .itext section, serves to decrypt the sections using a password acquired from command line arguments.
 Figure 8. The decryption routine is at sub_41B000
Figure 8. The decryption routine is at sub_41B000
 Figure 9. Identify the keyword ‘-pass’ in the command line
Figure 9. Identify the keyword ‘-pass’ in the command line
- Following the decryption of the text section, the .itext section undergoes a transformation, and the analyzed sample ultimately comprises four distinct functions.
 Figure 10. Compare the difference between the unpacked one (Left) and the packed one (Right) – Part 1
Figure 10. Compare the difference between the unpacked one (Left) and the packed one (Right) – Part 1
 Figure 11. Compare the difference between the unpacked one (Left) and the packed one (Right) – Part 2
Figure 11. Compare the difference between the unpacked one (Left) and the packed one (Right) – Part 2
2. T1027 Obfuscated Files or Information
-
- To enhance obfuscation, LockBit3.0 employs the following techniques to increase the complexity of analysis:
A. Utilizing String Hash Matching
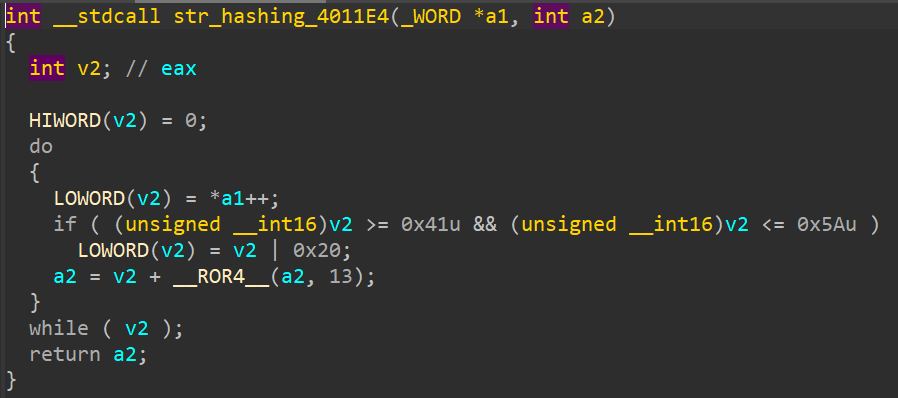 Figure 12. The string hash function is at 0x4011E4
Figure 12. The string hash function is at 0x4011E4
B. Implementing Stack String Obfuscation
 Figure 13. The string decrypt function is at 0x401260
Figure 13. The string decrypt function is at 0x401260
3. T1027.007 Dynamic API Resolution
-
- In order to rebuild the Import Address Table (IAT), LockBit3.0 employs a highly intricate approach.
 Figure 14. The function for reconstructing IAT is at 0x408254
Figure 14. The function for reconstructing IAT is at 0x408254
-
- The process of reconstructing the IAT involves three stages:
A. Identifying DLLs within the system memory using string hashes.
B. Extracting the API address by parsing the InLoadOrderModuleList and comparing the API name hash.
C. Arbitrarily selecting one of the five available stubs for IAT reconstruction. Each stub retrieves the genuine API address through a circular shift and XOR operation using a hardcoded key.
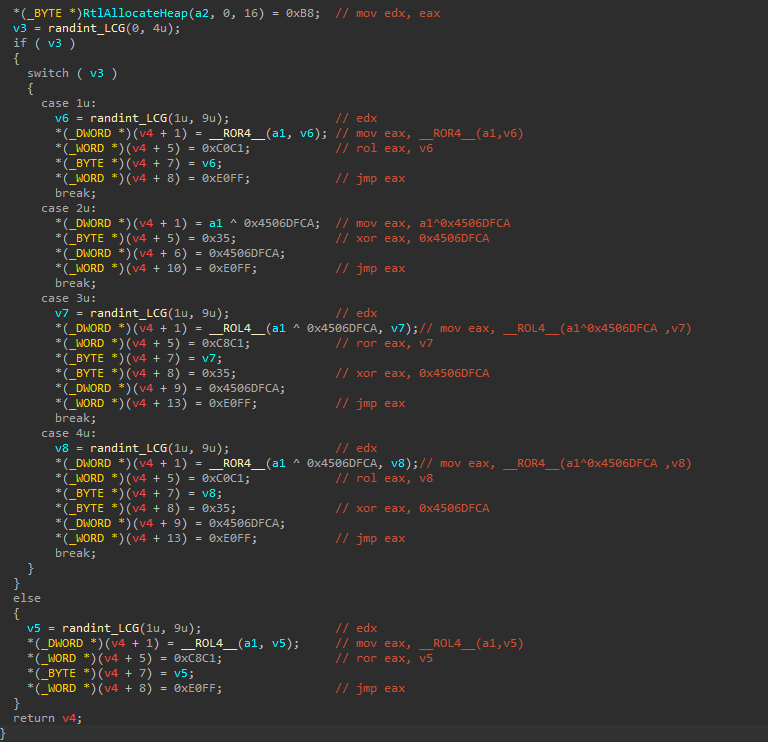 Figure 15. The preparation of the obfuscated API addresses is actually an invertible operation
Figure 15. The preparation of the obfuscated API addresses is actually an invertible operation
4. T1614.001 System Location Discovery: System Language Discovery
-
- LockBit3.0 incorporates a code snippet originating from BlackMatter/Darkside. If the detected language is among the following: Russian (0x419), Ukrainian (0x22), Belarusian (0x23), etc., the execution will be halted.
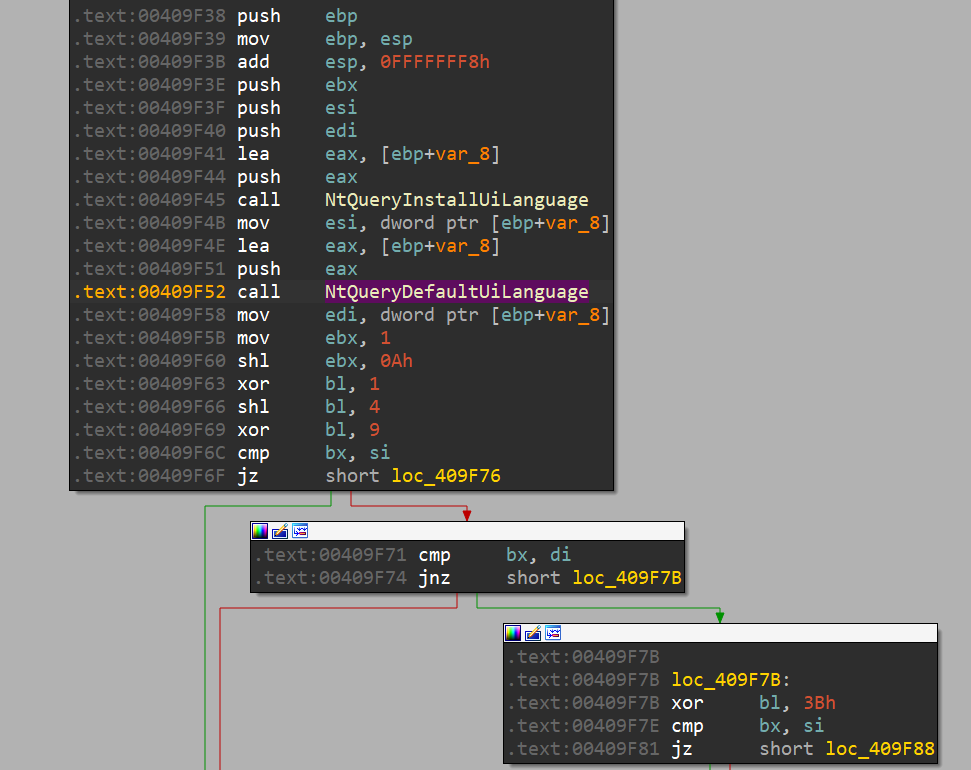 Figure 16. The code snippet of language checking is the same as BlackMatter/Darkside
Figure 16. The code snippet of language checking is the same as BlackMatter/Darkside
5. T1490 Inhibit System Recover
-
- In order to hinder the recovery of encrypted files from shadow copies, LockBit3.0 also terminates and removes the VSS service. Subsequently, it eliminates the shadow copies of disks utilizing the WMI interface.
 Figure 17. Delete shadow copies through WMI
Figure 17. Delete shadow copies through WMI
6. T1562.001 Impair Defenses: Disable or Modify Tools
-
- To disable Windows Defender, the analyzed sample replicates the access token of the Trusted Installer Service, which is authorized to halt Windows Defender. Utilizing this access token, it can effectively stop and remove services associated with Windows Defender.
 Figure 18. Stops the services matched to one of the string hashes
Figure 18. Stops the services matched to one of the string hashes
7. T1070.001 Indicator Removal: Clear Windows Event Logs
-
- To eradicate traces in the Windows Event Log, the analyzed sample clears the event logs and ceases the corresponding services, ensuring that no evidence remains.
 Figure 19. The decrypted stack strings for Windows Event Log
Figure 19. The decrypted stack strings for Windows Event Log
 Figure 20. LockBit3.0 clears the event log with ClearEventLogW()
Figure 20. LockBit3.0 clears the event log with ClearEventLogW()
 Figure 21. Terminates and deletes Windows Event Log services
Figure 21. Terminates and deletes Windows Event Log services
8. T1489 Service Stop
-
- To halt processes, LockBit3.0 utilizes the Windows API function TerminateProcess.
- To cease services, LockBit3.0 employs the Windows API functions ControlService and DeleteService.
 Figure 22. The stopped services and processes in the analyzed sample
Figure 22. The stopped services and processes in the analyzed sample
9. T1486 Data Encrypted for Impact
-
- LockBit3.0 incorporates a multithreading file encryption approach through the use of IoCompletionPort.
 Figure 23. Creates multiple threads for file encryption
Figure 23. Creates multiple threads for file encryption
 Figure 24. The main logic for handling multithreading file encryption
Figure 24. The main logic for handling multithreading file encryption
-
- Throughout the execution process, the ransom note remains obfuscated until it is ultimately written to the file.
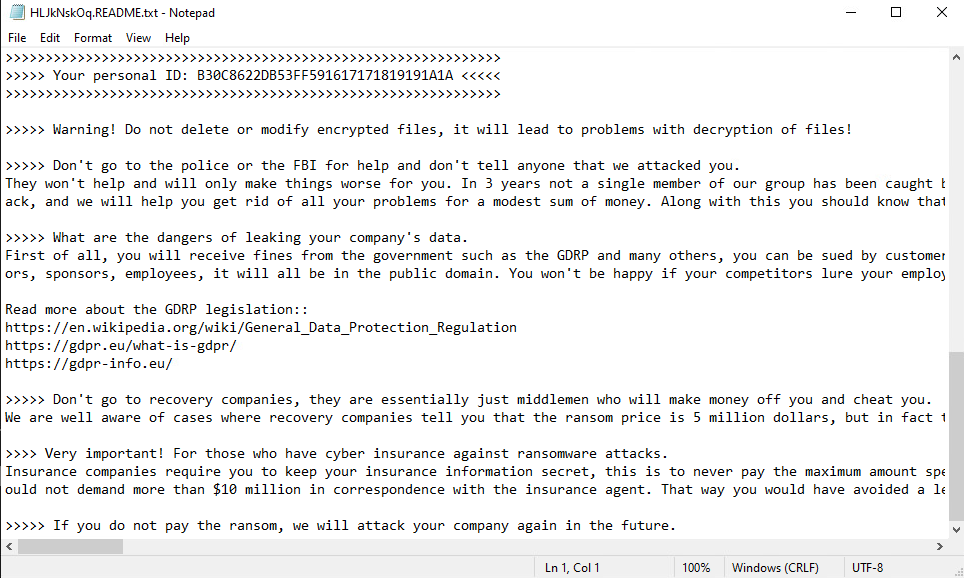 Figure 25. The ransom note of LockBit3.0
Figure 25. The ransom note of LockBit3.0
 Figure 26. The ransom note in memory
Figure 26. The ransom note in memory
-
- The analyzed sample saves the icon and wallpaper within the C:\ProgramData directory.
![]() Figure 27. The icon of LockBit3.0
Figure 27. The icon of LockBit3.0
 Figure 28. The wallpaper of LockBit3.0
Figure 28. The wallpaper of LockBit3.0
2 Lockbit 3.0 Security Recommendations
1. Stellar can detect LockBit 3.0 ransomware with Realtime Scanning
Stellar is the first solution to provide uninterrupted protection and comprehensive oversight for both legacy and modernized assets operating concurrently. By utilizing the advanced threat scan of real time scanning, it is possible to detect malicious software in real-time. Upon detection of such software, it will display event log messages, informing the name, path, and security risk of the infected file.
 Figure 29. LockBit3.0 quarantined by Stellar
Figure 29. LockBit3.0 quarantined by Stellar
2. Stellar can prevent the execution of LockBit ransomware by Application Lockdown
Stellar provides support for application lockdown, which can prevent programs, DLL files, drivers, and scripts that are not explicitly included in the approved application list from running. By blocking malicious software and preventing accidental use, Stellar ensures operational integrity, reduces downtime, and provides cost savings through increased flexibility, especially for systems that cannot be patched.
 Figure 30. The execution of LockBit3.0 blocked by Stellar
Figure 30. The execution of LockBit3.0 blocked by Stellar
Indicators of Compromise (IoCs)
| Description | Filename | SHA256 |
| Encryptor | {04830965-76E6-6A9A-8EE1-6AF7499C1D08}.exe | 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce |
| Encryptor | 506f3b12853375a1fbbf85c82ddf13341cf941c5acd4a39a51d6addf145a7a51 |
Reference
[1] NorthwaveSecurity, GitHub – NorthwaveSecurity/lockbit3: An assortment of scripts used in the analysis of Lockbit 3.0, NorthwaveSecurity’s GitHub, Accessed Feb 26, 2023
[2] Ivan Nicole Chavez, Byron Gelera, Katherine Casona, Nathaniel Morales, Ieriz Nicolle Gonzalez, Nathaniel Gregory Ragasa, LockBit Ransomware Group Augments Its Latest Variant, LockBit 3.0, With BlackMatter Capabilities, TrendMicro, July 25, 2022
[3] Chuong Dong, Darkside Ransomware, Chuong Dong’s Blog, May 6, 2021
[4] Chuong Dong, BlackMatter Ransomware v2.0, Chuong Dong’s Blog, Sep 5, 2021
[5] Dana Behling, https://blogs.vmware.com/security/2022/10/lockbit-3-0-also-known-as-lockbit-black.html, VMware, Oct 15, 2022
[6] Alexandre Mundo, LockBit3.0: A Threat that Persists, Trellix, Nov 17, 2022
[7] Jim Walter, LockBit 3.0 Update | Unpicking the Ransomware’s Latest Anti-Analysis and Evasion Techniques, SentinalOne, Jul 21, 2022





