Magniber Ransomware Overview
The Magniber ransomware was first identified in late 2017 when it was discovered using the Magnitude Exploit Kit to conduct malvertising attacks against users in South Korea. However, it has remained active since then, continually updating its tactics by employing new obfuscation techniques and methods of evasion. In April 2022, Magniber gained notoriety for disguising itself as a Windows update file to lure victims into installing it. It then began spreading via JavaScript in September 2022.
According to the observations of TXOne Networks’ threat research, although Magniber has been active since 2017, it had only begun to impact critical infrastructure and smart manufacturing in the third quarter of 2022. In this analysis, we will examine a classic ransomware sample with a SHA1 hash value of ec7404efa1deb47b9ffce7a23e2b08c8156c64f4, which exists in the form of a Windows Installer Package (.msi) when obtained. We will analyze its execution process as follows:
Figure 1. Attack Flow Diagram of Magniber
Attack Flow Diagram of Magniber
Table 1 illustrates Magniber’s attack tactics and technical content using the MITRE ATT&CK framework for clarity.
Table 1. MITRE ATT&CK Tactics and Techniques
| MITRE Tactics | MITRE Techniques | Description | |
| ID | Techniques | ||
| Execution | T1204.002 | User Execution–Malicious File | Magniber disguises itself as a .msi file software installer to lure users into opening it. |
| T1106 | Native API | Magniber uses native Windows syscalls to make analysis more difficult. | |
| Privilege Escalation | T1055.009 | Thread Execution Hijacking | Magniber enumerates processes and injects shellcode into them to execute encryption with higher privileges. |
| T1574.011 | Services Registry Permissions Weakness | Magniber overwrites the reference registry upon execution of fodhelper.exe. | |
| T1548.002 | Bypass User Account Control | Magniber overwrites the registry of fodhelper.exe to bypass UAC and execute the malicious VBScript with administrator privilege. | |
| Defense Evasion | T1140 | Files or Information | To evade detection, Magniber utilizes a technique of encoding VBScript and disguising it as a .jpg file. Once it has successfully evaded detection, Magniber then decodes the VBScript and executes it. |
| T1497.003 | Time Based Evasion | Magniber sleeps for random intervals to evade sandbox or antivirus detection. | |
| Impact | T1486 | Data Encrypted for Impact | Magniber encrypts the files on the computer. |
| T1490 | Inhibit System Recovery | Magniber modifies the boot options. | |
Magniber Ransomware Technical Analysis
The perpetrators of the Magniber ransomware campaign employed several tactics to evade detection and counteract prevention measures. In the following section, we provide a technical analysis of the ransomware:
1. Execution
1.1 T1204.002 Malicious File
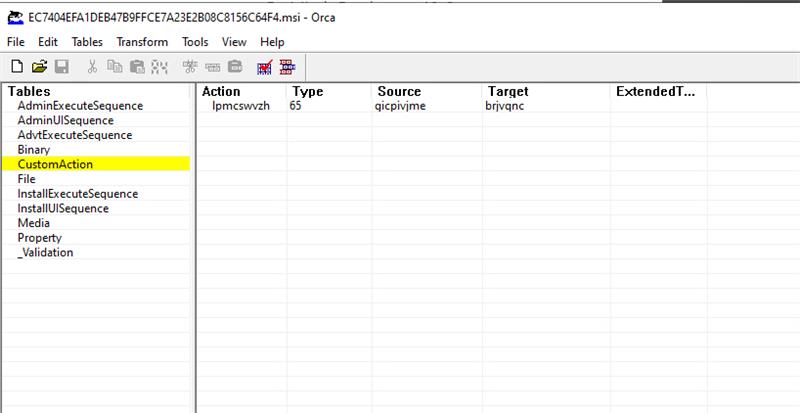
When the victim executes the 433e89.MSI, which is disguised as a Microsoft update file, the MSI will call CustomAction to execute the exported function brjvqnc of the DLL embedded in the MSI.
Figure 2. Embedded binary in the sample
Figure 3. CustomAction information in the sample
2. Defense Evasion
T1140 Deobfuscate/Decode Files or Information
In its anti-recovery routine, Magniber decodes and then overwrites the registry of fodhelper.exe to bypass UAC and execute the malicious VBScript with administrator privileges. Once it has successfully evaded detection, Magniber then decodes the VBScript and executes it. In Figure 4, we decode the VBScript to gain an understanding of the steps it takes to execute commands.
Figure 4. The decoded VBScript used for anti-recovery
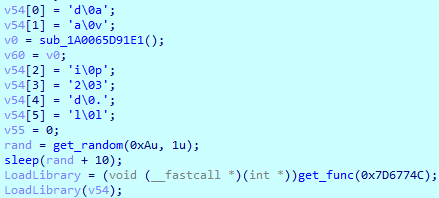
2.1 T1497.003 Time Based Evasion
In its file encryption routine, Magniber sleeps for random intervals using NtDelayExecution to evade analysis. The random sleep intervals may prevent sandbox or antivirus detection from succeeding.
Figure 5. Sleep for random seconds
Figure 6. Random generator
Figure 7. NtDelayExecution for sleeping functionality
Before proceeding to the anti-recovery routine, Magniber again sleeps for random intervals to evade detection.
Figure 8. Sleep again before anti-recovery
3. Impact
3.1 T1486 Data Encrypted for Impact and Ransomware Note
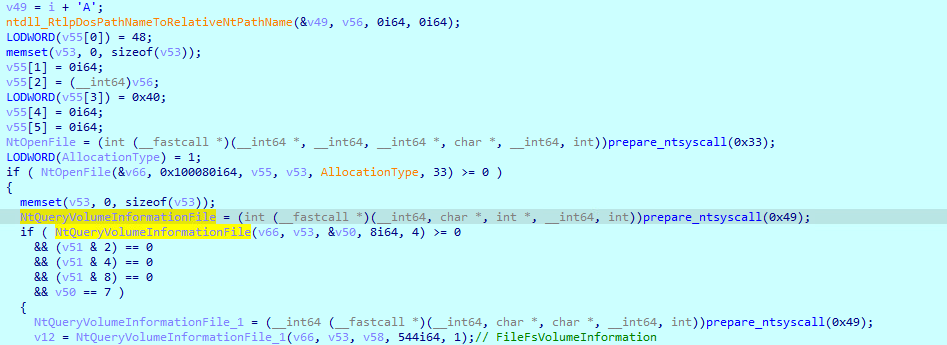
Compared to other ransomware, Magniber’s file encryption method is not very efficient as it encrypts files one by one.
Figure 9. NtQueryVolumeInformationFile with FileFsVolumeInformation
Figure 10. Enumerate files in the directory
The steps of file encryption are as follows:
- ReadFile
- WriteFile with the encrypted file content
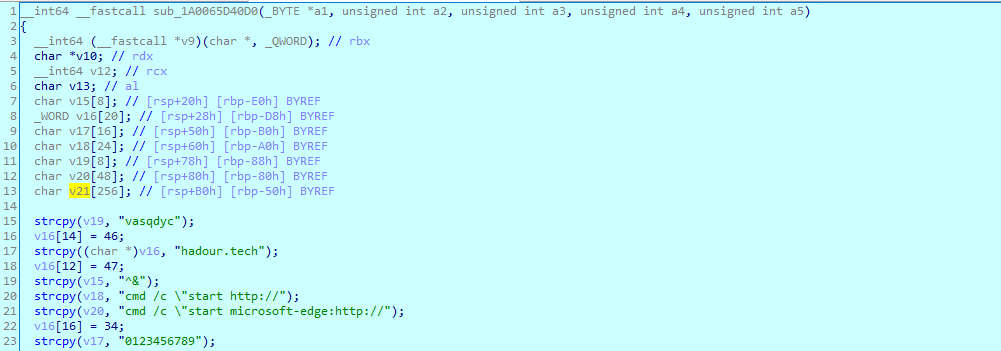
- WriteFile with the key blob
- Rename the file by adding the extension name .vasqdyc.
Figure 11. Get Cryptographic WinAPI function address from advapi32.dll
Figure 12. Setup key parameters for encrypting files
Figure 13. Read file for encryption
Figure 14. Write file for encryption
Figure 15. Rename encrypted files
Figure 16. Encrypt and rename the file by appending file extension name “.vasqdyc“
Figure 17. Create mutant with empty string
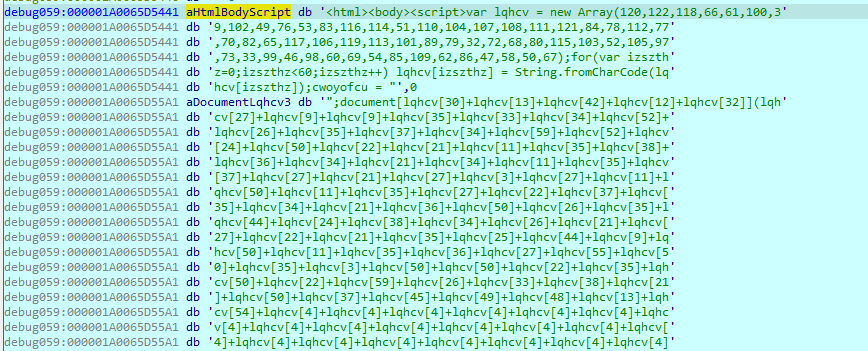
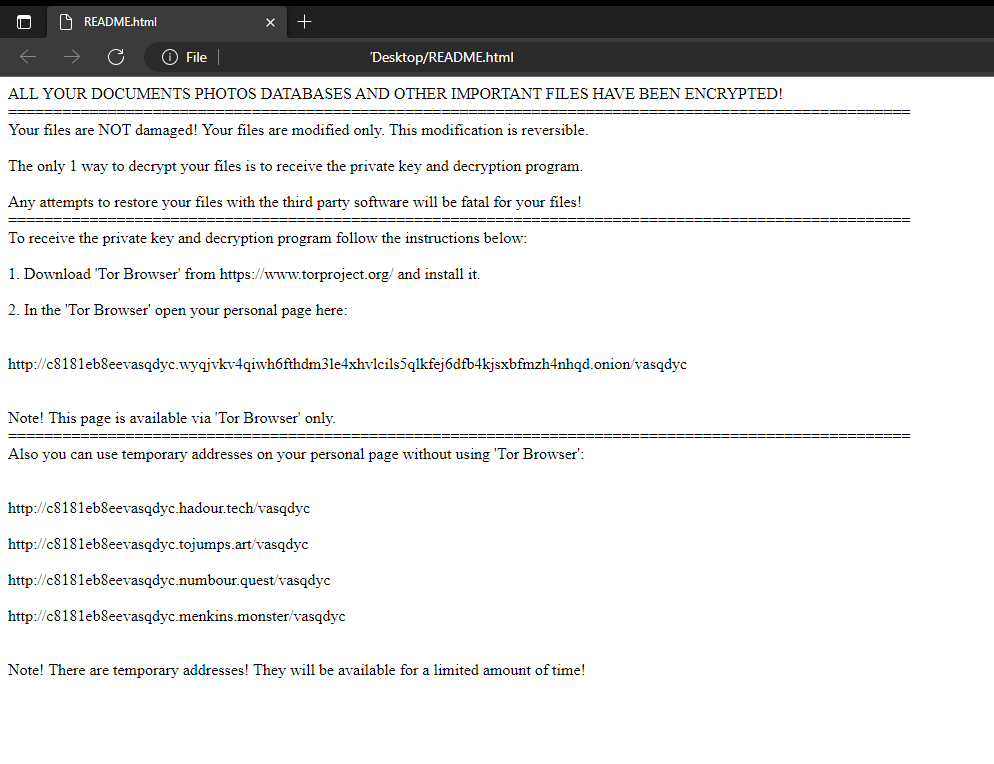
Magniber displays the ransom note by using the Microsoft-Edge URL protocol. Once the HTML body of the ransom note is loaded by Microsoft Edge, it will deobfuscate the content of the ransom note.
Figure 18. Show the ransom note by “microsoft-edge://”
Figure 19. Write ransom note by document.write in Javascript
Figure 20. Ransom note showed in Edge
Security Recommendation
1. The Magniber ransomware relies on tricking people into opening fake software updates. Enterprises are advised to be cautious about the source of all software and operating system security updates, and only download them from trusted sources such as Windows Update and official software vendor websites. It is also advisable to avoid executing files from unknown sources.
2. It is recommended to review whether there are abnormal work schedules and abnormal files on important servers or computers.
3. It is recommended to tighten network access controls. If possible, it is recommended to create a trusted list and only allow clients to access certain categories of websites while blocking access to other nonessential external network services.
4. It is advisable to deploy OT IPS/IDS and protection functions such as TXOne Networks when provided with a supplementary rule “1231503 FILE Abnormal Microsoft MSI File Transfer (suspicious)”to detect obfuscated MSI Ransomware. This allows enterprises to make use of industrial control IPS to monitor and filter activities such as suspicious intranet proliferation within the network,.
5. Restrict the login sources and methods for high-privileged administrator accounts. For example, follow the principle of least privilege by only using administrator accounts when performing privileged tasks, or restrict privileged accounts to allow login only from secure management hosts.
6. Deploy multi-level endpoint solutions, such as the advanced malicious program detection functions in TXOne’s Stellar endpoint solution. In addition to detecting specific threats, implementing Stellar’s application lockdown and behavior monitoring can prevent the execution of script files and unauthorized system changes.
7. Regularly back up corporate data. It is recommended to follow the 3-2-1 principle by properly backing up important files with three copies, stored in two different types of devices, with one copy located in a remote or secure location.
Indicators of Compromise (IoCs)
| Filename | SHA256 |
| 433e89.msi | 2edafe324bbeec87dba04c61032a04815227dcf472f98411a2cd8d377651e862 |
| MSIC3EB.tmp | 2196fa848c393869bdfd53100c3cb4d789e879f83cb464f5ccd72c75807cfc0a |
| soucfyuwwkr.jpg | e7ca83fc4415d068652b6fc9847389d25ecac8a09be81e097e95cadc0ad32d00 |
| Registry Key | Value |
| HKEY_CURRENT_USER\SOFTWARE\Classes\ AppX04g0mbrz4mkc6e879rpf6qk6te730jfv\Shell\Open\command\(Default) |
wscript.exe /B /E:VBScript.Encode ../../Users/Public/soucfyuwwkr.jpg |
| HKEY_CURRENT_USER\SOFTWARE\Classes\ AppX04g0mbrz4mkc6e879rpf6qk6te730jfv \Shell\Open\command\DelegateExecute |
None |
| HKEY_CURRENT_USER\SOFTWARE\Classes\ms-settings\CurVer(Default) | ppX04g0mbrz4mkc6e879rpf6qk6te730jfv |
References
[1] HP Threat Research Blog – “Magniber Ransomware Adopts JavaScript, Targeting Home Users with Fake Software Updates”, HP, October 13, 2022.
[2] Mateusz “j00ru” Jurczyk– “Windows X86-64 System Call Table (XP/2003/Vista/2008/7/2012/8/10)”, j00ru//vx tech blog, Accessed Dec 16, 2022.
[3] Llalum Victoria, Henry Alarcon Jr., John Rey Canon, Jay Nebre– “Abuse of Custom Actions in Windows Installer MSI”, TrendMicro, April 23, 2019
[4] Cybereason Global SOC Team – “Threat Analysis: MSI – Masquerading as a Software Installer”, Cybereason, December 5, 2022.
[5] John Hammond – “vbe-decoder: A Python3 script to decode an encoded VBScript file, often seen with a .vbe file extension”, GitHub, Accessed Dec 16, 2022.